How to Encrypt Files, Folders and Disks on Linux
- Last updated: Sep 21, 2025

In this guide, we will explore data encryption on GNU/Linux. Linux offers numerous tools to protect sensitive information, allowing you to encrypt individual files, secure containers, or even entire disks.
The use cases for encryption are diverse. For example, full-disk encryption protects your data against physical theft, ensuring that an attacker cannot access your information if the device is stolen. File encryption, on the other hand, is ideal for securely sharing confidential documents over untrusted channels such as email. Container-based encryption is useful when you want to create a secure, isolated storage area inside an otherwise unencrypted disk.
- In this guide, I will provide practical examples using the following tools, each suited for specific purposes:
- LUKS: For encrypting entire disks or secure containers
- OpenSSL or GnuPG: For encrypting individual files
How to Encrypt Files on Linux
Here, I will show you how to encrypt files on Linux using two different tools: OpenSSL and GnuPG.
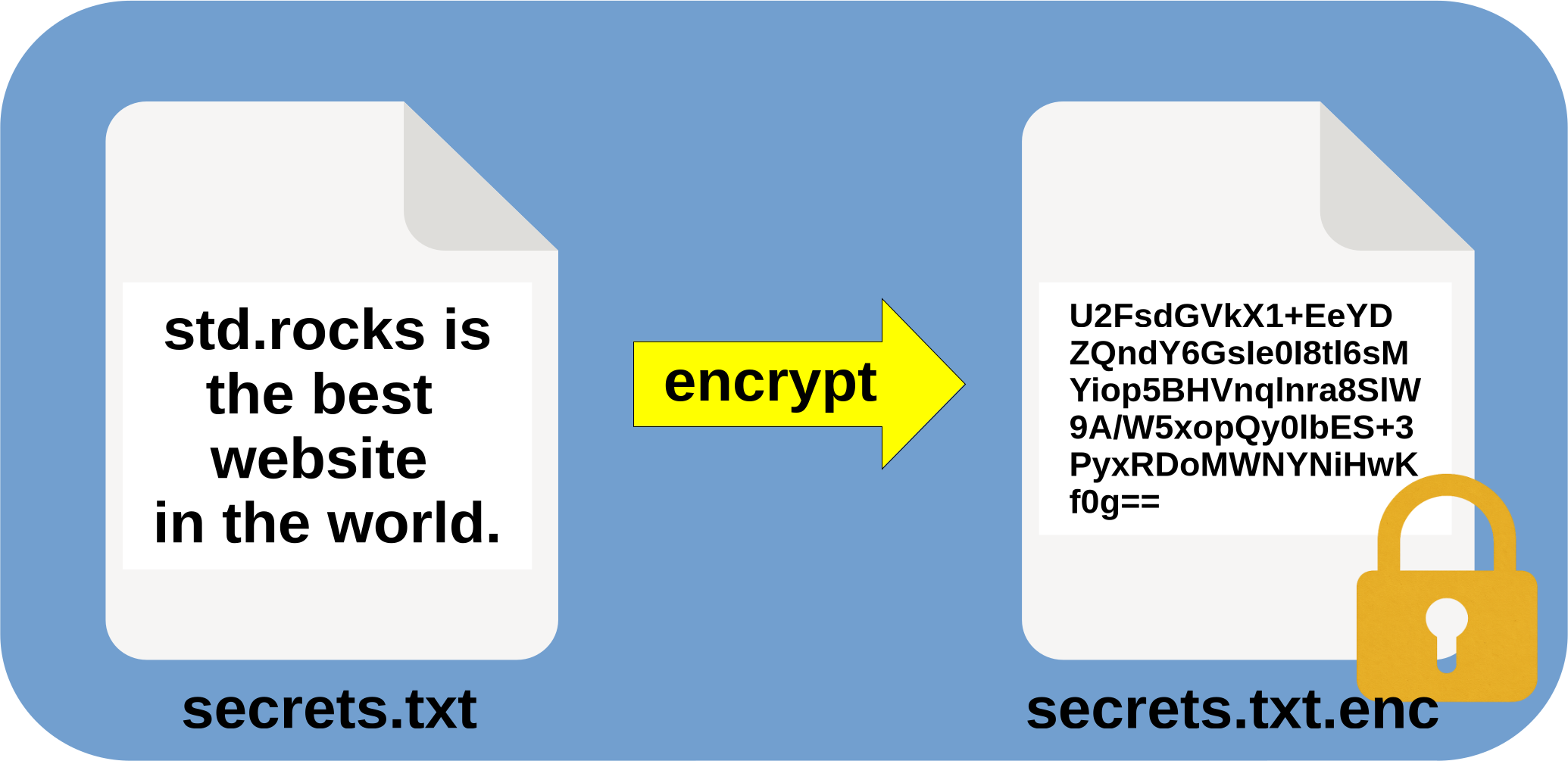
How to Encrypt Files Using OpenSSL on Linux
To encrypt files on Linux using OpenSSL, we will apply the following recommended options for strong security:
-aes-256-cbc: Uses the AES algorithm with a 256-bit key in Cipher Block Chaining (CBC) mode for robust encryption.-pbkdf2: Employs the PBKDF2 algorithm to derive a secure key from the password, enhancing resistance to brute-force attacks.-iter 200000: Specifies 200,000 iterations for PBKDF2, increasing the computational cost of brute-force attempts.-md sha256: Uses SHA-256 as the hashing algorithm for key derivation, ensuring secure key generation.-salt: Adds a random salt to protect against rainbow table attacks.
🔐 Example: encrypting secrets.txt into secrets.txt.enc:
user@host:~$ openssl enc -aes-256-cbc -pbkdf2 -iter 200000 -md sha256 -salt -in secrets.txt -out secrets.txt.enc
enter AES-256-CBC encryption password:JohnWeakP@sswd:)
Verifying - enter AES-256-CBC encryption password:JohnWeakP@sswd:)🔓 Example: decrypting secrets.txt.enc back to secrets.txt:
user@host:~$ openssl enc -d -aes-256-cbc -pbkdf2 -iter 200000 -md sha256 -salt -in secrets.txt.enc -out secrets.txt
enter AES-256-CBC decryption password:JohnWeakP@sswd:)How to Encrypt Files Using GnuPG on Linux
Another way to encrypt files on Linux is by using GnuPG with a symmetric cipher:
--symmetric: Encrypts with a symmetric cipher using a passphrase.--s2k-cipher-algo AES256: Sets AES-256 as the symmetric encryption algorithm.--s2k-digest-algo SHA512: Uses SHA-512 as the digest algorithm for key derivation.--s2k-count 1048576: Applies 1,048,576 iterations to strengthen the passphrase against brute-force attacks.
🔐 Example: encrypt the file secrets.txt into secrets.txt.gpg:
user@host:~$ gpg --symmetric --s2k-cipher-algo AES256 --s2k-digest-algo SHA512 --s2k-count 1048576 -o secrets.txt.gpg secrets.txt🔓 Example: decrypt secrets.txt.gpg back into secrets.txt:
user@host:~$ gpg --output secrets.txt --decrypt secrets.txt.gpgHow to Encrypt a File Container on Linux
Encrypted container will allow us to protect files and directory in a same space. Indeed, it will allow us to put any files inside.
How to Create and Initialize an Encrypted File Container on Linux
The first step is to create an encrypted container on Linux using dd.
A container is simply a regular file that will later be formatted and mounted as a virtual disk.
- In this example, we create a file named
containerin the root directory (/container). Its size is 1 GiB and it is filled with random data to ensure security:
root@host:~# dd if=/dev/urandom of=/container bs=1M count=1024 iflag=fullblock status=progressNext, we need to set up a loop device. A loop device on Linux allows us to map a regular file (such as our container) to a virtual block device, making it behave like a real disk.
- Check the first available loop device:
root@host:~# losetup -f- Map the
containerfile to the/dev/loop0loop device:
root@host:~# losetup /dev/loop0 /container- Install the
cryptsetuppackage, which provides the LUKS encryption tools:
root@host:~# apt update && apt install cryptsetup- Format the loop device with LUKS to initialize encryption:
root@host:~# cryptsetup luksFormat /dev/loop0
WARNING!
========
This will overwrite data on /dev/loop0 irrevocably.
Are you sure? (Type 'yes' in capital letters): YES
Enter passphrase for /container:JohnWeakP@sswd:)
Verify passphrase:JohnWeakP@sswd:)- Open (decrypt) the loop device with LUKS and map it to a virtual device named
decrypted_container:
root@host:~# cryptsetup luksOpen /dev/loop0 decrypted_container
Enter passphrase for /container:JohnWeakP@sswd:)- Format the new container with the file system of your choice (here ext4):
root@host:~# mkfs.ext4 /dev/mapper/decrypted_container- When finished, close the LUKS device and detach the loop device:
root@host:~# cryptsetup luksClose /dev/mapper/decrypted_containerroot@host:~# losetup -d /dev/loop0Your encrypted container is now successfully created, formatted, and ready for use on Linux.
How to Mount the Encrypted Container and Copy Files on Linux
Now let’s see how to mount and use the encrypted container we created earlier.
- Check the first available loop device:
root@host:~# losetup -f- Map the
containerfile to the/dev/loop0loop device:
root@host:~# losetup /dev/loop0 /container- Unlock the loop device with LUKS and map it to
decrypted_container:
root@host:~# cryptsetup luksOpen /dev/loop0 decrypted_container
Enter passphrase for /container:JohnWeakP@sswd:)- Mount the decrypted container to
/mnt/container:
root@host:~# mkdir -p /mnt/container; mount /dev/mapper/decrypted_container /mnt/container- You can now use
/mnt/containerlike any mounted device. For example, copy a file into it:
root@host:~# cp file.txt /mnt/container/Encrypt a Disk on Linux
We can also encrypt an entire disk using LUKS on Linux, providing full-disk protection for all files and partitions.

Initialize an Encrypted Disk
- Since we will format the disk, it is critical to correctly identify the device you want to encrypt before proceeding:
root@host:~# fdisk -l
Disk /dev/sdb: 465,76 GiB, 500107862016 bytes, 976773168 sectors
Disk model: Samsung SSD 850
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disk /dev/sda: 465,76 GiB, 500107862016 bytes, 976773168 sectors
Disk model: Samsung SSD 850
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: gpt
Disk identifier: B06AF5D8-B51A-4688-98DC-C91E51E85AE0
Device Start End Sectors Size Type
/dev/sda1 2048 2000895 1998848 976M EFI System
/dev/sda2 2000896 79704063 77703168 37.1G Linux filesystem
/dev/sda3 79704064 83884031 4179968 2G Linux swap- Create a GPT partition table on
/dev/sdband add a single partition:
root@host:~# fdisk /dev/sdb
Welcome to fdisk (util-linux 2.41).
Changes will remain in memory only, until you decide to write them.
Be careful before using the write command.
Device does not contain a recognized partition table.
Created a new DOS (MBR) disklabel with disk identifier 0x2e1f330d.
create a GPT partition table
Command (m for help): g
Created a new GPT disklabel (GUID: 1BB9BB8D-14D8-411D-B398-8A1C6F125FB6).
create a new partition
Command (m for help): n
press Enter to accept the defaults
Partition number (1-128, default 1):
press Enter to accept the defaults
First sector (2048-67108830, default 2048):
press Enter to accept the defaults
Last sector, +/-sectors or +/-size{K,M,G,T,P} (2048-976773168, default 976773168):
Created a new partition 1 of type 'Linux filesystem' and of size 465 GiB.
write changes to disk and exit
Command (m for help): w- Install the
cryptsetuppackage, which provides the LUKS encryption tools:
root@host:~# apt update && apt install cryptsetup- Format the disk partition
/dev/sdb1with LUKS to initialize encryption:
root@host:~# cryptsetup luksFormat /dev/sdb1
WARNING!
========
This will overwrite data on /dev/sdb1 irrevocably.
Are you sure? (Type 'yes' in capital letters): YES
Enter passphrase for /dev/sdb1:JohnWeakP@sswd:)
Verify passphrase:JohnWeakP@sswd:)- Open the encrypted partition
/dev/sdb1with LUKS and map it to a virtual device nameddecrypted_disk:
root@host:~# cryptsetup luksOpen /dev/sdb1 decrypted_disk
Enter passphrase for /dev/sdb1:JohnWeakP@sswd:)- Format the unlocked device with the file system of your choice (here ext4):
root@host:~# mkfs.ext4 /dev/mapper/decrypted_disk- Close the encrypted partition
decrypted_disk:
root@host:~# cryptsetup luksClose /dev/mapper/decrypted_diskMount an Encrypted Disk
Once the disk has been initialized and encrypted, we can mount it on our system.
- Open the encrypted partition
/dev/sdb1with LUKS and map it to a virtual device nameddecrypted_disk:
root@host:~# cryptsetup luksOpen /dev/sdb1 decrypted_disk
Enter passphrase for /dev/sdb1:JohnWeakP@sswd:)- Finally, mount the decrypted disk on
/mnt/disk:
root@host:~# mkdir -p /mnt/disk; mount /dev/mapper/decrypted_disk /mnt/disk