Elastic Stack 8 - Installer et Configurer Elasticsearch + Kibana sur Debian Linux
- Mise à jour le 08 mai 2024

Un SIEM ou Gestion de l'information des événements de sécurité est une solution de sécurité permettant de centraliser des journaux et des événements de nombreux périphériques différents d'un réseau informatique dans le but de les traiter et de générer des alertes dans le cas ou des événements anormaux se produiraient.
Nous vérons ici comment déployer la solution Elastic Stack. Qui a l'avantage d'être en grande partie gratuite.
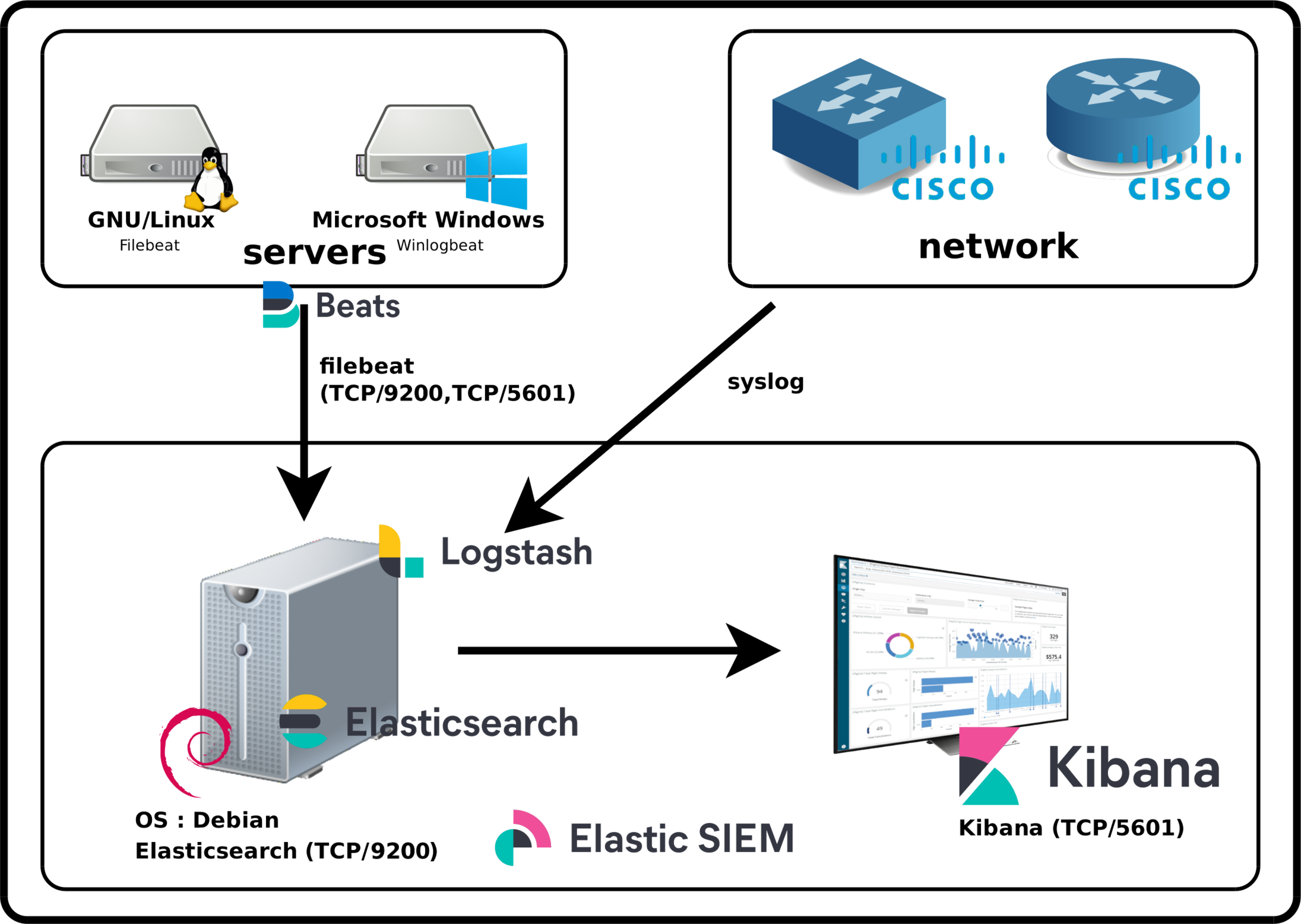
Elastic Stack Architecture
Elasticsearch est un moteur de recherche et d'analyse distribué pour tout type de données.
Kibana est un outil de visualisation et de gestion des données pour Elasticsearch. Kibana sera utilisé pour rechercher, visualiser, et interagir avec les données stockées dans Elasticsearch.
Notes
Versions
- OS : Debian
- Elasticsearch : 8
Les liens
- Liens de téléchargement : https://www.elastic.co/
- Guide Officiel : https://www.elastic.co/guide/
- Les différentes éditions de la suite Elastic https://www.elastic.co/subscriptions
Les composants
Principaux
- Elasticsearch : La recherche et l'analyse RESTful distribuées. (Le cerveau de la solution).
- Kibana : Visualisez vos données. Naviguez dans la Suite. (Affichage, représentation graphique).
- Beats : Collecte, analyse et transfert léger.
Autres
- Logstash : Ingestion, transformation, enrichissement et sortie. (Récupérer un flux d'information avec possibilité de le transformer/filtrer avant de le transmettre à Elasticsearch).
- Filebeat : Récupérer les informations des fichiers journaux. (Transmettre des fichiers journaux d'une machine vers Elasticsearch.)
Les ports par défaut
- ElastiSearch : http://IP_ADDRESS:9200
- Kibana web access : http://IP_ADDRESS:5601
- Logstash : 9600
Installer Elasticsearch (Debian Server)
Prérequis
- Installer apt-transport-https et les paquets nécessaires :
root@host:~# apt update && apt-get install apt-transport-https gnupg curl wget- Importer la clé PGP Elasticsearch :
root@host:~# wget -qO - https://artifacts.elastic.co/GPG-KEY-elasticsearch | gpg --dearmor -o /usr/share/keyrings/elasticsearch-keyring.gpg- Ajouter le dépot elastic :
root@host:~# echo "deb [signed-by=/usr/share/keyrings/elasticsearch-keyring.gpg] https://artifacts.elastic.co/packages/8.x/apt stable main" | tee /etc/apt/sources.list.d/elastic-8.x.listElasticsearch
- Installer Elasticsearch et noter le mot de passe super-utilisateur :
root@host:~# apt update && apt-get install elasticsearch[…]
--------------------------- Security autoconfiguration information ------------------------------
Authentication and authorization are enabled.
TLS for the transport and HTTP layers is enabled and configured.
The generated password for the elastic built-in superuser is : elastic_password;)
If this node should join an existing cluster, you can reconfigure this with
'/usr/share/elasticsearch/bin/elasticsearch-reconfigure-node --enrollment-token <token-here>
after creating an enrollment token on your existing cluster.
You can complete the following actions at any time:
Reset the password of the elastic built-in superuser with
'/usr/share/elasticsearch/bin/elasticsearch-reset-password -u elastic'.
Generate an enrollment token for Kibana instances with
'/usr/share/elasticsearch/bin/elasticsearch-create-enrollment-token -s kibana'.
Generate an enrollment token for Elasticsearch nodes with
'/usr/share/elasticsearch/bin/elasticsearch-create-enrollment-token -s node'.
-------------------------------------------------------------------------------------------------
Kibana
- Installer Kibana :
root@host:~# apt update && apt-get install kibanaConfiguring
Elasticsearch
- Éditer le fichier /etc/elasticsearch/elasticsearch.yml pour paramétrer l'interface d'écoute :
network.host: 0.0.0.0- Démarrer le service elasticsearch :
root@host:~# systemctl start elasticsearch.service- Vérifier que le service elastic fonctionne :
root@host:~# curl --cacert /etc/elasticsearch/certs/http_ca.crt -u elastic https://localhost:9200
Enter host password for user 'elastic': elastic_password;)
{
"name" : "std",
"cluster_name" : "elasticsearch",
"cluster_uuid" : "StdgreaTBanDKphU4S0ceg",
"version" : {
"number" : "8.13.3",
"build_flavor" : "default",
"build_type" : "deb",
"build_hash" : "ff17057114c2199c9c1bbecc727003a907c0db7a",
"build_date" : "2024-04-29T22:05:16.051731935Z",
"build_snapshot" : false,
"lucene_version" : "9.10.0",
"minimum_wire_compatibility_version" : "7.17.0",
"minimum_index_compatibility_version" : "7.0.0"
},
"tagline" : "You Know, for Search"
}Kibana
- Éditer le fichier /etc/kibana/kibana.yml pour paramétrer l'adresse d'écoute sur «toutes les adresses» :
server.host: "0.0.0.0"
server.publicBaseUrl: "http://X.X.X.X:5601"- Démarrer le service :
root@host:~# systemctl start kibana.service- Créer le jeton d'inscription :
root@host:~# /usr/share/elasticsearch/bin/elasticsearch-create-enrollment-token -s kibana
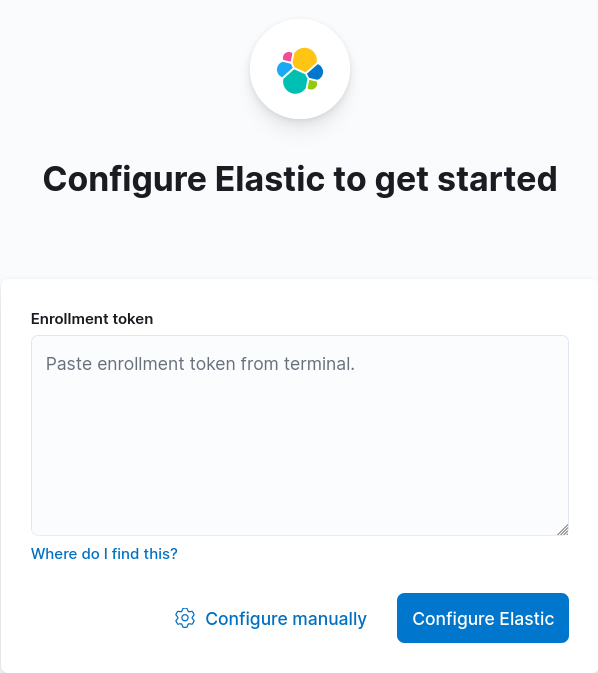
eyJ2ZXIiOiI4LjEuMiIsImFkciI6WyIxOTIuMTY4LjEuNjY6OTIwMCJdLCJmZ3IiOiJmYzdiZmFmMjNmODEzN2M1NmY4YTg1NGMxNTdjMWFkYTNiZDdiOGM4NTE4YTZhNmI3wWNiYzBkNzc0ZTRjNzc1Iiwia2V5Ijoib1ZBTkVJQUIxWVNBT0BiUWVsUVc6cEU1WXF3U1FTUENjcFFaZUJvTGtKdyJ0- Ouvrir Firefox à l'adresse http://X.X.X.X:5601 et coller le jeton d'inscription puis cliquer sur Configure Elastic :
- Générer un code de vérification Kibana :
root@host:~# /usr/share/kibana/bin/kibana-verification-code
Your verification code is: 139 477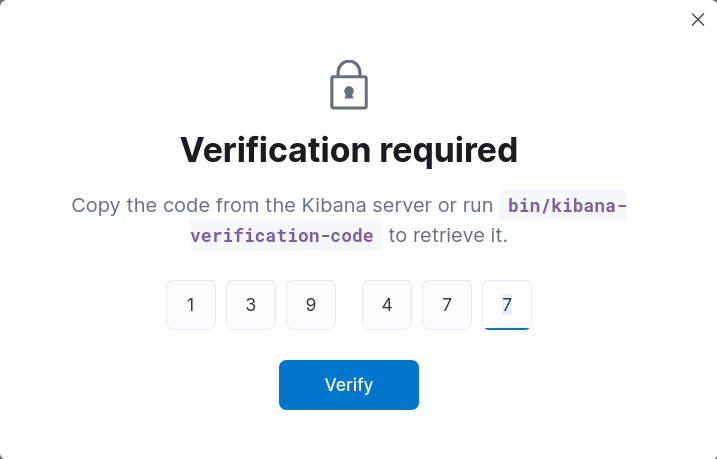
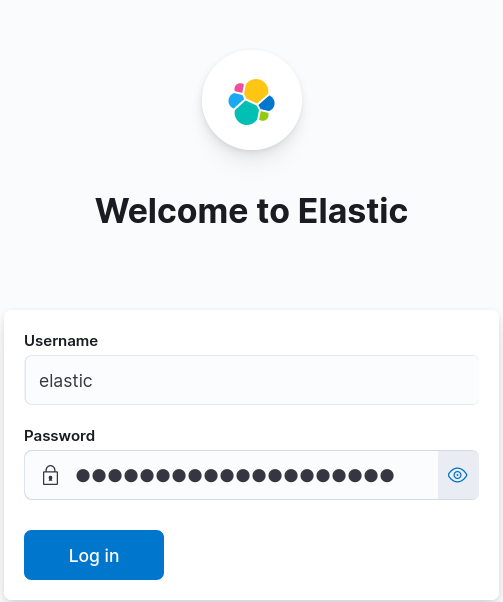
- Nous pouvons maintenant nous connecter à Kibana avec le compte elastic :
Sécuriser Kibana
Une des grosses améliorations de la version 8 est qu'elasticsearch est maintenant sécurisé lors de l'installation par défaut afin de chiffrer ses communications.
Ce n'est pas le cas de Kibana pour lequel nous nous connectons par défaut en http. Nous allons donc voir comment activer la connexion https.
- Commenter la ligne suivante afin de désactiver l'OpenSSL Legacy Provider en éditant le fichier /etc/kibana/node.options :
## enable OpenSSL 3 legacy provider
#--openssl-legacy-provider- Lancer le script kibana-encryption-keys et copier les valeurs en dessous de la ligne settings :
root@host:~# /usr/share/kibana/bin/kibana-encryption-keys generate
## Kibana Encryption Key Generation Utility
The 'generate' command guides you through the process of setting encryption keys for:
xpack.encryptedSavedObjects.encryptionKey
Used to encrypt stored objects such as dashboards and visualizations
https://www.elastic.co/guide/en/kibana/current/xpack-security-secure-saved-objects.html#xpack-security-secure-saved-objects
xpack.reporting.encryptionKey
Used to encrypt saved reports
https://www.elastic.co/guide/en/kibana/current/reporting-settings-kb.html#general-reporting-settings
xpack.security.encryptionKey
Used to encrypt session information
https://www.elastic.co/guide/en/kibana/current/security-settings-kb.html#security-session-and-cookie-settings
Already defined settings are ignored and can be regenerated using the --force flag. Check the documentation links for instructions on how to rotate encryption keys.
Definitions should be set in the kibana.yml used configure Kibana.
Settings:
xpack.encryptedSavedObjects.encryptionKey: caeb7879368e3dd66d7302f6810daec1
xpack.reporting.encryptionKey: c1c89f500966ac710f7fa5eaf2939976
xpack.security.encryptionKey: e1458d710ffb321e4a4f4eb792c78b2b- Coller les lignes précédentes dans le fichier /etc/kibana/kibana.yml :
[…]
xpack.encryptedSavedObjects.encryptionKey: caeb7879368e3dd66d7302f6810daec1
xpack.reporting.encryptionKey: c1c89f500966ac710f7fa5eaf2939976
xpack.security.encryptionKey: e1458d710ffb321e4a4f4eb792c78b2b- Obtenir le mot de passe du conteneur http.p12 :
root@host:~# /usr/share/elasticsearch/bin/elasticsearch-keystore show xpack.security.http.ssl.keystore.secure_password
592l_UJGSXmliJIvuokDab- Extraire les certificats nécessaires :
root@host:~# cd /etc/kibana/root@host:~# openssl pkcs12 -in /etc/elasticsearch/certs/http.p12 -out server.crt -clcerts -nokeys
Enter Import Password:592l_UJGSXmliJIvuokDabroot@host:~# openssl pkcs12 -in /etc/elasticsearch/certs/http.p12 -out server.key -nocerts -nodes
Enter Import Password:592l_UJGSXmliJIvuokDabroot@host:~# chown root:kibana /etc/kibana/server.*root@host:~# chmod g+r /etc/kibana/server.*- Éditer le fichier /etc/kibana/kibana.yml :
server.ssl.enabled: true
server.ssl.certificate: /etc/kibana/server.crt
server.ssl.key: /etc/kibana/server.key- Redémarrer le service kibana :
root@host:~# systemctl restart kibana.serviceAttendre quelques secondes puis se connecter à kibana à l'adresse https://X.X.X.X:5601
Démarrage automatique
Pour que les services Elasticsearch et Kibana se lancent au démarrage, nous avons besoin de procéder à quelques paramétrages supplémentaires.
Elasticsearch
- Activer le démarrage automatique du service Elasticsearch :
root@host:~# systemctl enable elasticsearch.serviceKibana
- Activer le démarrage automatique du service Kibana :
root@host:~# systemctl enable kibana.serviceFichiers de Log
- Elasticsearch :
root@host:~# tail /var/log/elasticsearch/elasticsearch.log- Kibana :
root@host:~# tail /var/log/kibana/kibana.log