root@host:~# apt-get install strongswan strongswan-pki
On utilisera les ipsec pki tools dans le but de créer notre CA. Les certificats seront placés dans /etc/ipsec.d/ :
root@host:~# cd /etc/ipsec.d/ root@host:~# ipsec pki --gen --type rsa --size 4096 --outform pem > private/strongswanKey.pem root@host:~# chmod 600 private/strongswanKey.pem root@host:~# ipsec pki --self --ca --lifetime 3650 --outform pem --in private/strongswanKey.pem --type rsa --dn "C=FR, O=strongSwan, CN=strongSwan Root CA" > cacerts/strongswanCert.pem
root@host:~# cd /etc/ipsec.d/ root@host:~# ipsec pki --gen --type rsa --size 2048 --outform pem > private/vpnHostKey.pem root@host:~# chmod 600 private/vpnHostKey.pem root@host:~# ipsec pki --pub --in private/vpnHostKey.pem --type rsa | ipsec pki --issue --lifetime 3650 --outform pem --cacert cacerts/strongswanCert.pem --cakey private/strongswanKey.pem --dn "C=FR, O=strongSwan, CN=vpn.shebangthedolphins.net" --san vpn.shebangthedolphins.net --flag serverAuth --flag ikeIntermediate > certs/vpnHostCert.pem
root@host:~# cd /etc/ipsec.d/ root@host:~# ipsec pki --gen --type rsa --size 2048 --outform pem > private/ClientKey.pem root@host:~# chmod 600 private/ClientKey.pem root@host:~# ipsec pki --pub --in private/ClientKey.pem --type rsa | ipsec pki --issue --lifetime 3650 --outform pem --cacert cacerts/strongswanCert.pem --cakey private/strongswanKey.pem --dn "C=FR, O=strongSwan, CN=ss.vpn@shebangthedolphins.net" --san ss.vpn@shebangthedolphins.net > certs/ClientCert.pem root@host:~# openssl pkcs12 -export -name "My own VPN client certificate" -inkey private/ClientKey.pem -in certs/ClientCert.pem -certfile cacerts/strongswanCert.pem -caname "strongSwan Root CA" -out Client.p12
config setup
conn %default
keyexchange=ikev1
ikelifetime=7200s
keylife=3600s
ike=aes128-sha1-modp4096
esp=aes128-sha1-modp4096
dpdaction=clear
dpddelay=300s
conn host-host
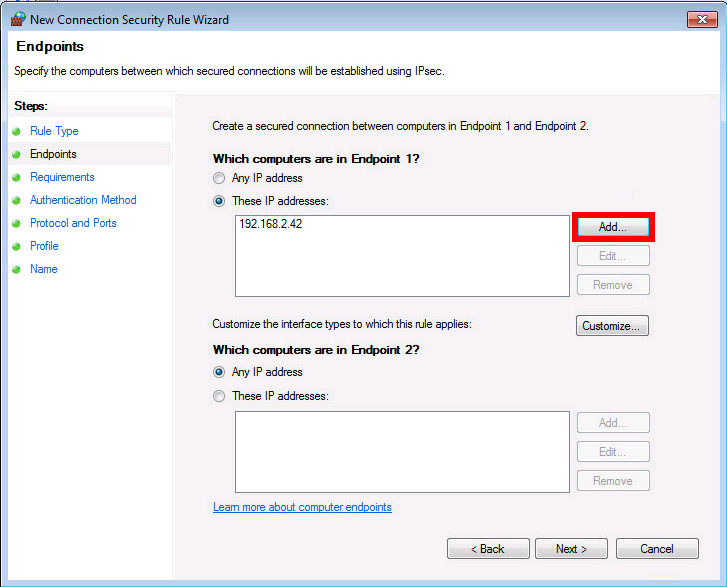
left=192.168.2.42
leftcert=vpnHostCert.pem
leftid=vpn.shebangthedolphins.net
leftsendcert=always
leftauth=pubkey
leftfirewall=yes
right=%any
rightid=%any
type=transport
auto=add
authby=pubkey
: RSA vpnHostKey.pem
user@alice # ipsec restart
user@alice # ipsec status
user@alice # ipsec statusall
user@alice # ipsec listcerts
user@alice # systemctl restart strongswan.service
user@alice # ipsec pki --print --in certs/vpnHostCert.pem
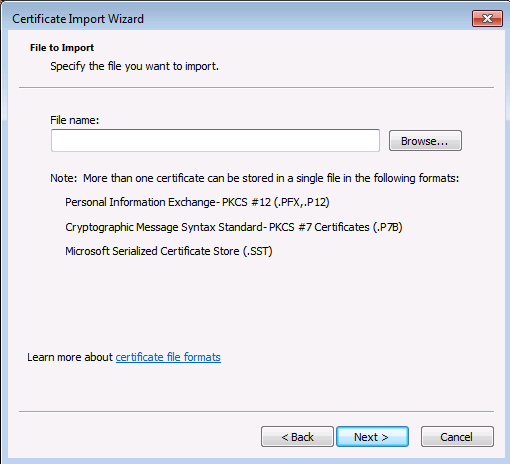
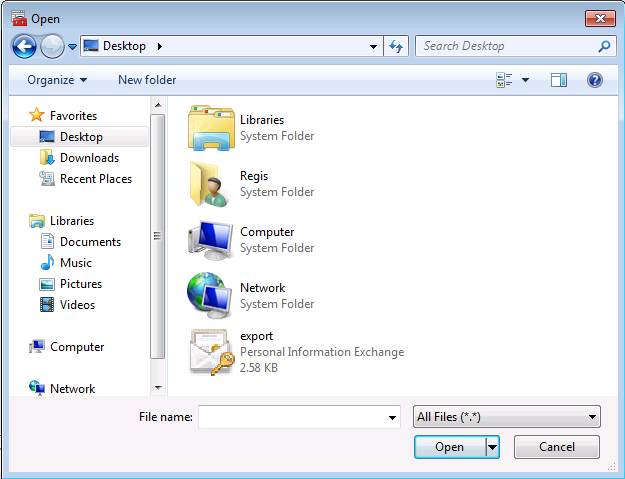
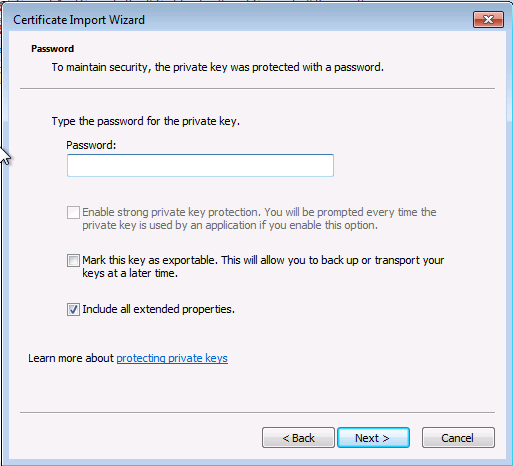
Dans un premier temps nous devons copier le fichier pk12 précédement créé vers notre station Windows.
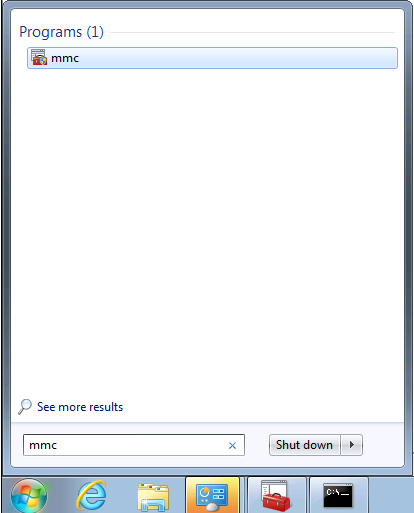
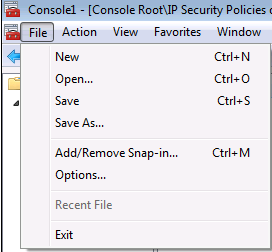
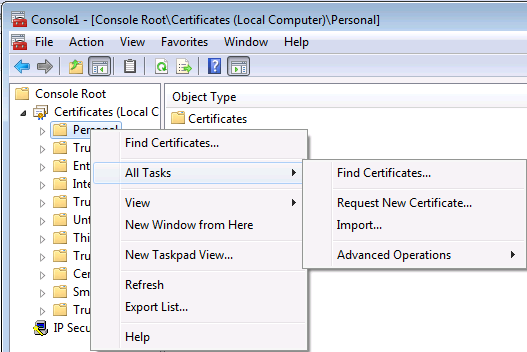
Ouvrir la Console MMC :
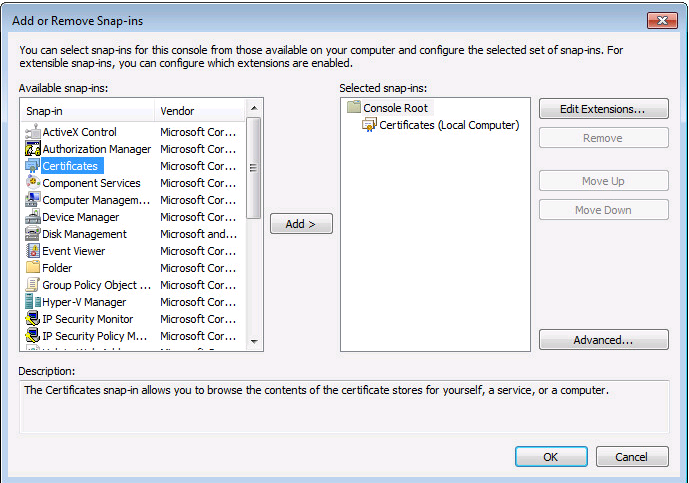
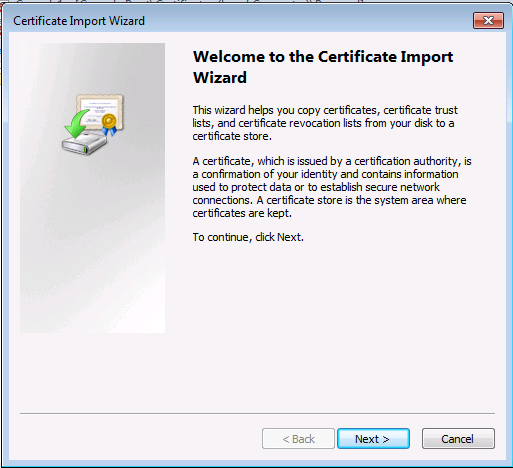
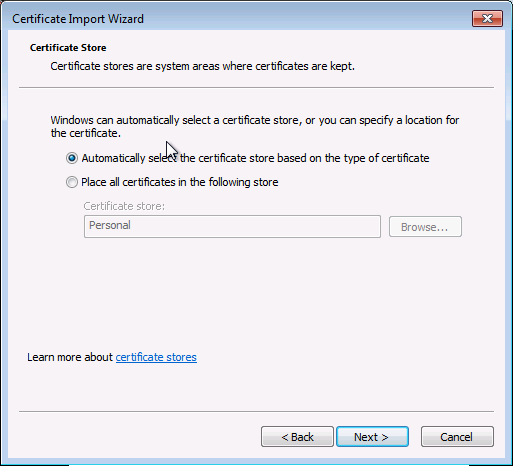
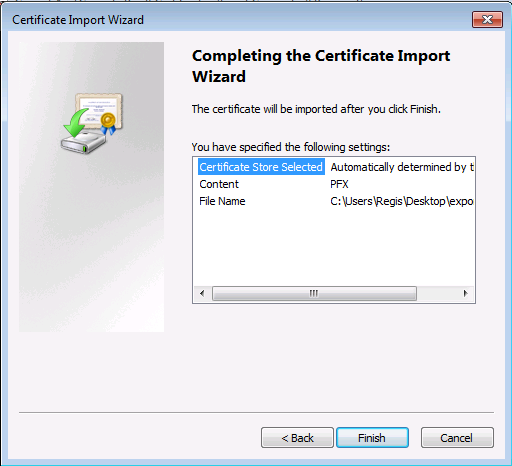
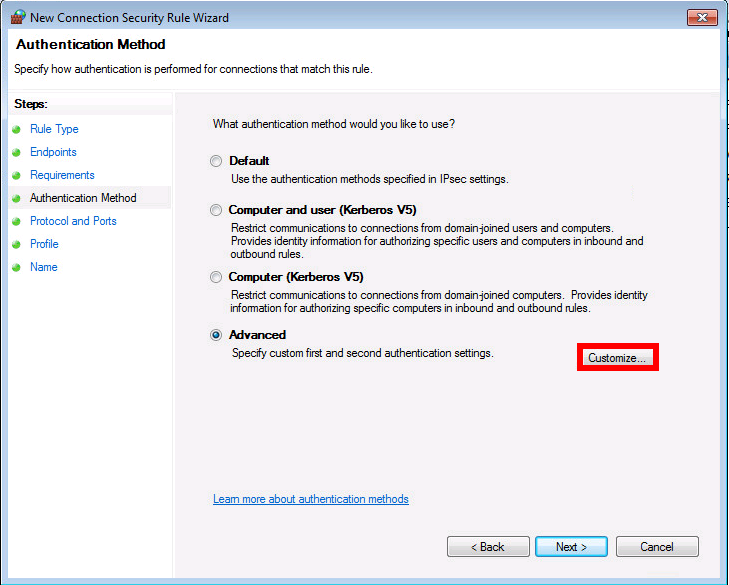
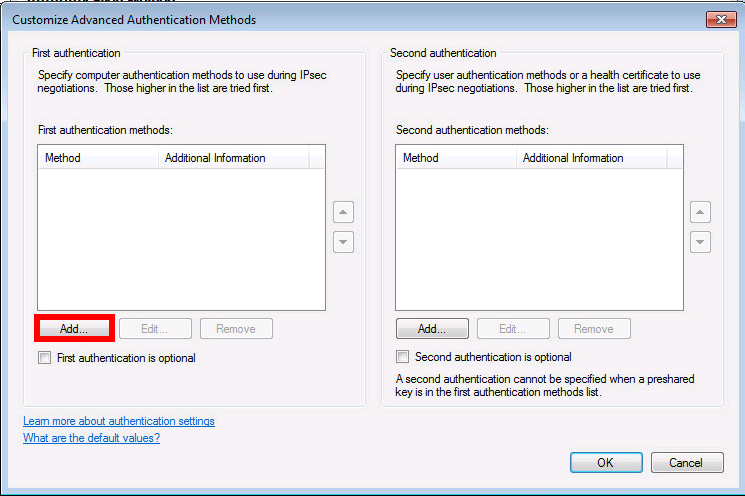
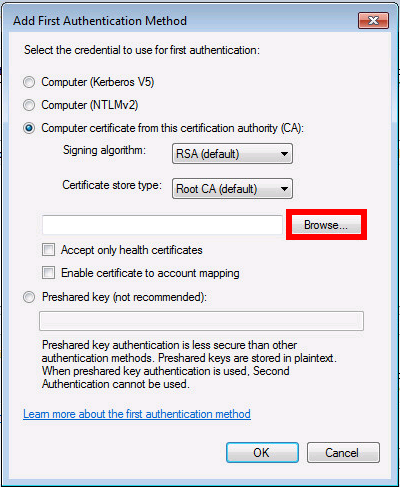
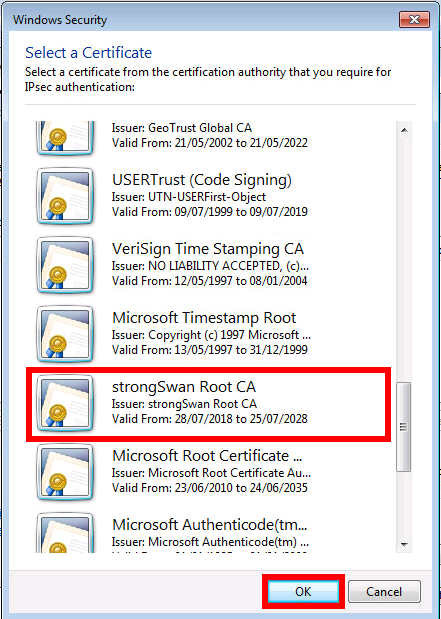
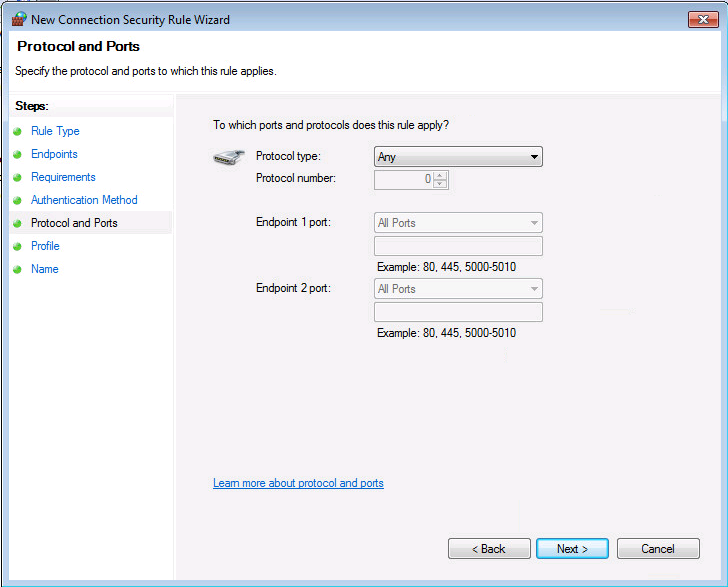
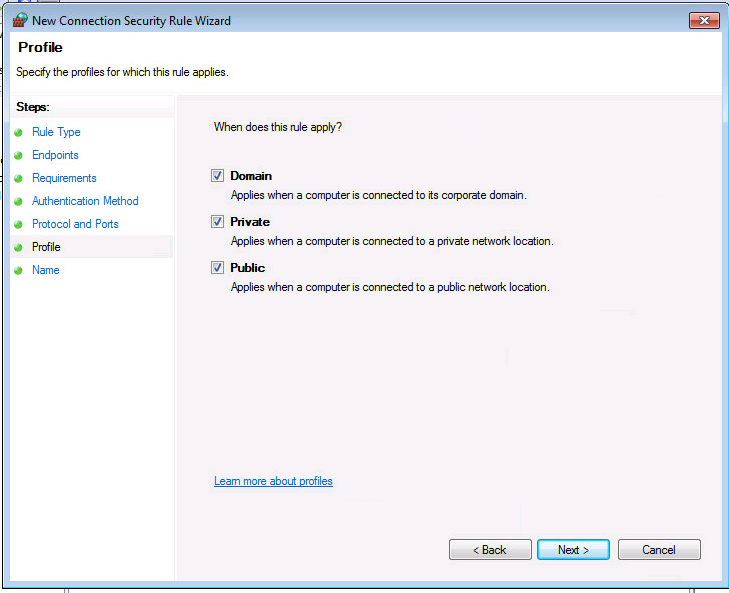
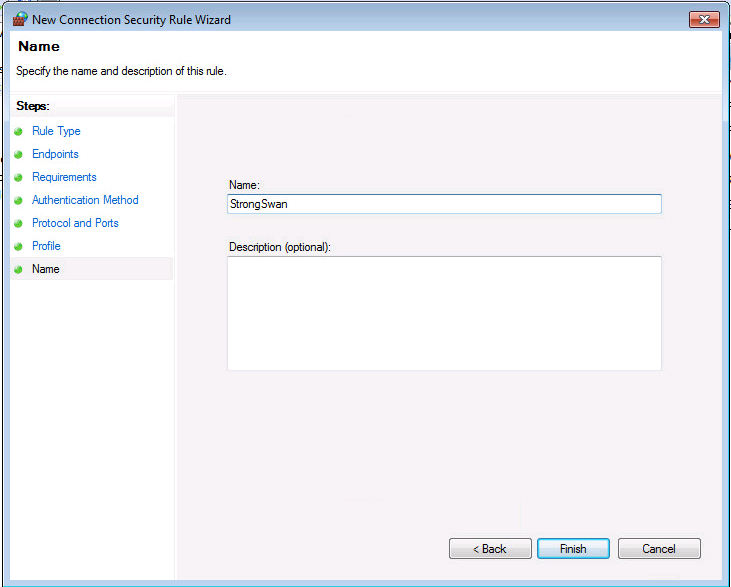
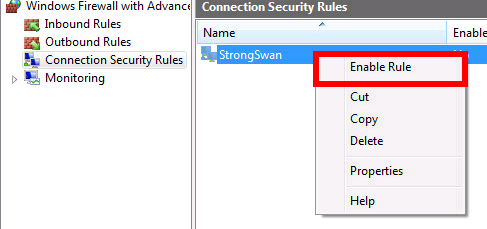
Installation du certificat
Contact :