How to Open and Mount BitLocker Partitions on Linux with Dislocker or Cryptsetup
- Last updated: Aug 20, 2025

On my new computer, I set up a dual boot with Windows and Kali Linux. For security, I enabled BitLocker to encrypt the Windows partition. Since the partition was encrypted, I needed a way to access it from Kali Linux, so I turned to the Dislocker tool.
As you’ll see, it’s quite straightforward to use.
Installing Dislocker to Access BitLocker Partitions
The installation steps below are shown on Kali Linux, but they work the same way on most Debian-based distributions (such as Ubuntu or Linux Mint).
- Install
dislockerwith the package manager:
$ sudo apt update && sudo apt install dislockerIdentify the BitLocker-Encrypted Partition on Linux
Once dislocker is installed, the next step is to locate the encrypted Windows partition. On Linux, this can be done using the fdisk tool.
- List all partitions with
fdisk:
$ sudo fdisk -l
Disk /dev/nvme0n1: 931,51 GiB, 1000204886016 bytes, 1953525168 sectors
Disk model: Samsung SSD 980 1TB
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 16384 bytes / 131072 bytes
Disklabel type: gpt
Disk identifier: 5A1C0C90-61D9-1BBV-96C1-7ED8C4EI8BA5
Device Start End Sectors Size Type
/dev/nvme0n1p1 2048 206847 204800 100M EFI System
/dev/nvme0n1p2 206848 239615 32768 16M Microsoft reserved
/dev/nvme0n1p3 239616 1022901873 1022662258 487,6G Microsoft basic data
/dev/nvme0n1p4 1022902272 1024237567 1335296 652M Windows recovery environment
/dev/nvme0n1p5 1024239616 1025216511 976896 477M Linux filesystem
/dev/nvme0n1p6 1025216512 1953523711 928307200 442,7G Linux filesystemThe partition labeled as Microsoft basic data with a size of 487.6 GB looks like the right candidate for our BitLocker volume. 🙂
Decrypt and Mount the BitLocker Partition
Depending on your hardware, you can decrypt the partition either with a PIN code or with the recovery password. If your system uses TPM (Trusted Platform Module), as in my case, you will need the recovery password.
- If TPM is enabled and you try to decrypt using the PIN code, you will encounter the following error message:
[CRITICAL] None of the provided decryption mean is decrypting the keys. Abort.
[CRITICAL] Unable to grab VMK or FVEK. Abort.Preparing Mount Points for Dislocker
- Create two mount points for dislocker — one for the unlocked container, and one for the actual Windows filesystem:
$ sudo mkdir /media/bitlocker && sudo chown user:user /media/bitlocker$ sudo mkdir /media/bitlockerloop && sudo chown user:user /media/bitlockerloopDecrypt the BitLocker Partition
- Decrypt with the recovery key (required if TPM is enabled):
$ sudo dislocker -V /dev/nvme0n1p3 -p181938-009977-030118-024662-878971-217634-366661-422744 -- /media/bitlocker- Decrypt with a PIN code (possible if TPM is disabled):
$ sudo dislocker -V /dev/nvme0n1p3 -u123456 -- /media/bitlockerMount the Decrypted BitLocker Partition
- Mount the unlocked
dislocker-file(created by Dislocker) as a loop device:
$ sudo mount -o loop -t ntfs /media/bitlocker/dislocker-file /media/bitlockerloop- Verify that you can now access the Windows partition:
$ ls -l /media/bitlockerloopDisable Windows Fast Startup to Avoid BitLocker Issues
To prevent data corruption when mounting the encrypted partition, and to avoid triggering BitLocker’s recovery mode (where you are asked to enter the recovery key), I recommend disabling the Fast Startup feature in Windows. More details are available on the VeraCrypt documentation page: Issues and Limitations.
- To do this, run the following PowerShell command in an administrator console:
PS > Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\Session Manager\Power\" -Name "HiberbootEnabled" -Value "0"- Or through the Windows Control Panel:
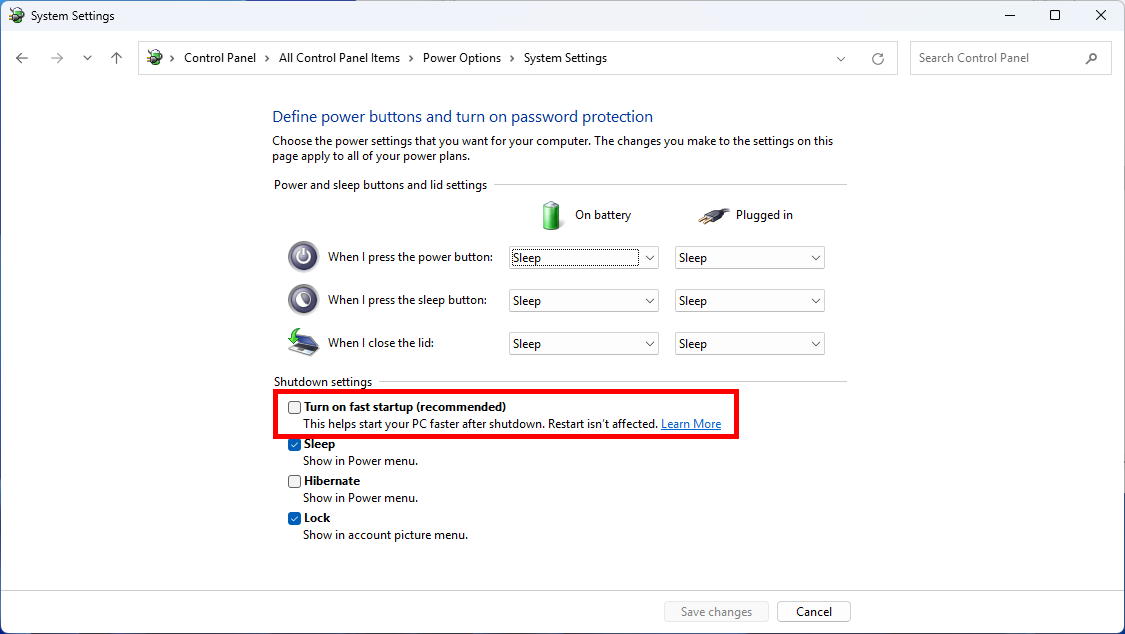
Troubleshooting and Alternatives
I recently ran into an issue while trying to open my Windows BitLocker partition. All of a sudden, the following error appeared when attempting to mount it through the loop device (which relies on the kernel NTFS3 driver):
mount: /media/bitlockerloop: wrong fs type, bad option, bad superblock on /dev/loop0, missing codepage or helper program, or other error.
- When checking the logs with
dmesg, several lines reportedI/O errormessages:
$ sudo dmesg
[ 1055.272722] loop: module loaded
[ 1055.274749] loop0: detected capacity change from 0 to 1022662258
[ 1055.275657] I/O error, dev loop0, sector 1022662016 op 0x0:(READ) flags 0x80700 phys_seg 1 prio class 0
[ 1055.276241] I/O error, dev loop0, sector 1022662016 op 0x0:(READ) flags 0x0 phys_seg 1 prio class 0
[ 1055.276248] Buffer I/O error on dev loop0, logical block 127832752, async page read
[ 1055.279496] EXT4-fs (loop0): VFS: Can't find ext4 filesystem
[ 1055.283152] I/O error, dev loop0, sector 1022662016 op 0x0:(READ) flags 0x80700 phys_seg 1 prio class 0
[ 1055.283413] EXT4-fs (loop0): VFS: Can't find ext4 filesystem
[ 1055.283691] I/O error, dev loop0, sector 1022662016 op 0x0:(READ) flags 0x80700 phys_seg 1 prio class 0
[ 1055.283736] I/O error, dev loop0, sector 1022662016 op 0x0:(READ) flags 0x0 phys_seg 1 prio class 0
[ 1055.283743] Buffer I/O error on dev loop0, logical block 511331008, async page read
[ 1055.283767] I/O error, dev loop0, sector 1022662018 op 0x0:(READ) flags 0x0 phys_seg 1 prio class 0
[ 1055.283771] Buffer I/O error on dev loop0, logical block 511331009, async page read
[ 1055.283799] I/O error, dev loop0, sector 1022662020 op 0x0:(READ) flags 0x0 phys_seg 1 prio class 0
[ 1055.283802] Buffer I/O error on dev loop0, logical block 511331010, async page read
[ 1055.283820] I/O error, dev loop0, sector 1022662022 op 0x0:(READ) flags 0x0 phys_seg 1 prio class 0
[ 1055.283823] Buffer I/O error on dev loop0, logical block 511331011, async page read
[ 1055.285259] I/O error, dev loop0, sector 1022662016 op 0x0:(READ) flags 0x0 phys_seg 1 prio class 0
[ 1055.285268] Buffer I/O error on dev loop0, logical block 511331008, async page read
[ 1055.285299] I/O error, dev loop0, sector 1022662018 op 0x0:(READ) flags 0x0 phys_seg 1 prio class 0
[ 1055.285305] Buffer I/O error on dev loop0, logical block 511331009, async page read
[ 1055.285322] Buffer I/O error on dev loop0, logical block 511331010, async page read
[ 1055.285337] Buffer I/O error on dev loop0, logical block 511331011, async page read
[ 1055.291290] EXT4-fs (loop0): VFS: Can't find ext4 filesystem
[ 1055.293359] FAT-fs (loop0): bogus number of reserved sectors
[ 1055.293365] FAT-fs (loop0): Can't find a valid FAT filesystemI ran smartctl to check the health of the disk, but it reported no issues. I also tried repairing the Windows filesystem with chkdsk /f /r, but the problem persisted. After some research, I found that this situation can occur, and the recommended solution is to use the NTFS-3G driver instead of the kernel NTFS3 driver.
Although dislocker itself was not responsible for the issue, I also discovered that since version 2.3.0, cryptsetup is capable of opening BitLocker-encrypted partitions. It’s always interesting to have multiple tools available, so I’ll show you how to use cryptsetup as an alternative.
- First, if not already installed, add the
ntfs-3gdriver andcryptsetup:
$ sudo apt update && sudo apt install ntfs-3g cryptsetup- Next, decrypt the BitLocker partition. Here I’ll use
cryptsetup, but you can also usedislockerif you prefer:
$ sudo cryptsetup open --type bitlk /dev/nvme0n1p3 bitlocker- Finally, mount the decrypted device using the
NTFS-3Gdriver (instead of the kernelNTFS3):
$ sudo ntfs-3g /dev/mapper/bitlocker /media/bitlocker/