How to Set Up a Syslog Server with Rsyslog on Debian to Centralize Logs
- Last updated: Nov 29, 2024

Intro
I recently needed to set up a syslog server to centralize the logs of my Cisco switches.
I'll describe here how to set up such a service under Debian in order to retrieve the switch logs.
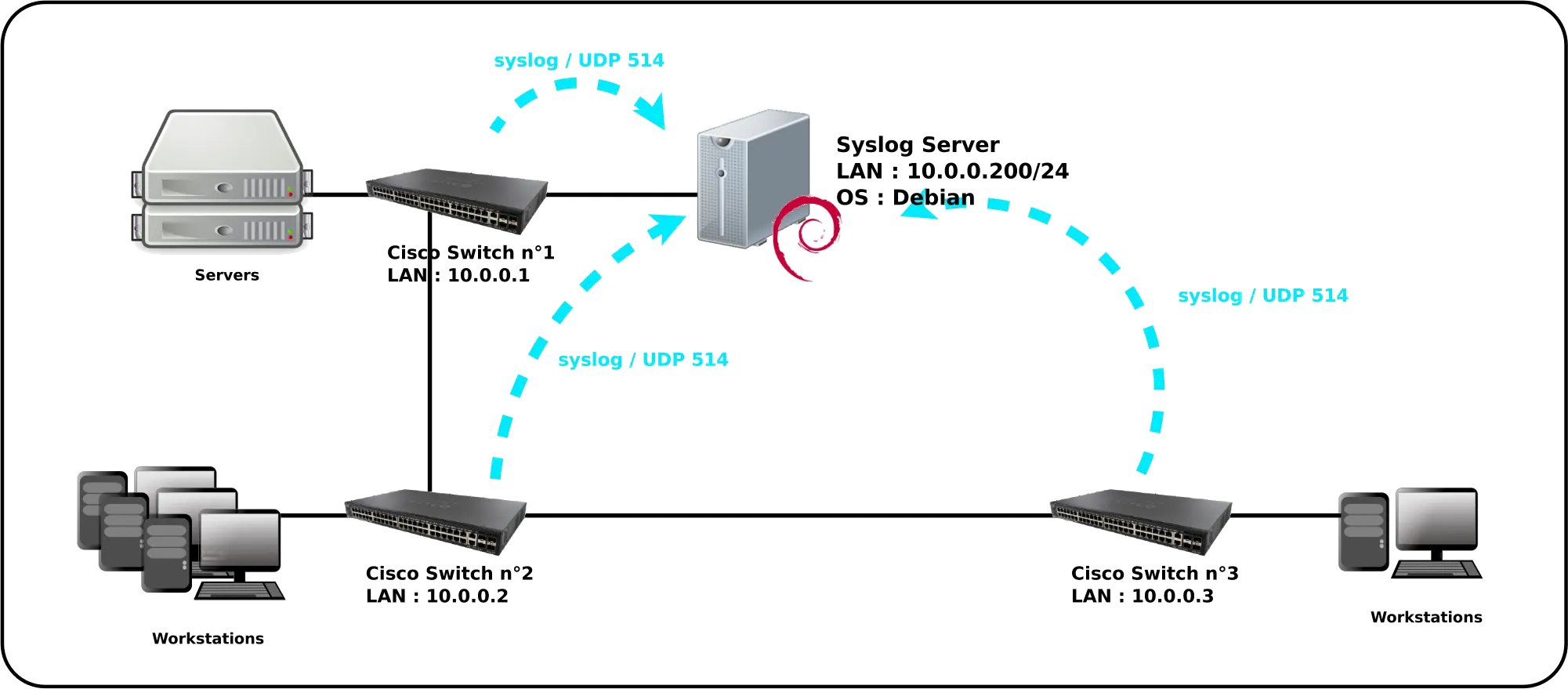
Network diagram
All switches will send their logs to the Debian Linux server.
By default, Cisco Switch logs are sent via the UDP protocol on port 514.
Configuring Cisco Switches
- Set up the network configuration of Cisco Switches:
Note: I also configure the gateway and DNS so that the switch is correctly configured to collect the correct time from any NTP server. The logs will therefore be correctly time-stamped.
Switch# conf t
Switch(config)# ip name-server 80.67.169.12
Switch(config)# ip domain lookup
Switch(config)# interface vlan1
Switch(config-if)# ip address 10.0.0.1 255.255.255.0
Switch(config-if)# no ip address dhcp
Switch(config-if)# ip default-gateway 10.0.0.254- Configure the remote syslog server:
Switch(config)# logging host 10.0.0.200Debian Server
First, we need to install a brand-new GNU/Linux Debian server. Then edit the /etc/rsyslog.conf file.
Installing and configuring rsyslog
- Install the rsyslog package:
root@host:~# apt update && apt install rsyslog- Edit the
/etc/rsyslog.conffile:
# /etc/rsyslog.conf configuration file for rsyslog
#
# For more information install rsyslog-doc and see
# /usr/share/doc/rsyslog-doc/html/configuration/index.html
#################
#### MODULES ####
#################
module(load="imuxsock") # provides support for local system logging
module(load="imklog") # provides kernel logging support
#module(load="immark") # provides --MARK-- message capability
# provides UDP syslog reception
module(load="imudp")
#input(type="imudp" port="514")
$UDPServerRun 514
# provides TCP syslog reception
#module(load="imtcp")
#input(type="imtcp" port="514")
#$InputTCPServerRun 514
###########################
#### GLOBAL DIRECTIVES ####
###########################
#
# Use traditional timestamp format.
# To enable high precision timestamps, comment out the following line.
#
$ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormat
#
# Set the default permissions for all log files.
#
$FileOwner root
$FileGroup adm
$FileCreateMode 0640
$DirCreateMode 0755
$Umask 0022
$AllowedSender UDP, 127.0.0.1, 10.0.0.0/24
#
# Where to place spool and state files
#
$WorkDirectory /var/spool/rsyslog
#
# Include all config files in /etc/rsyslog.d/
#
$IncludeConfig /etc/rsyslog.d/*.conf
#template
$template Incoming-logs,"/var/log/%HOSTNAME%/logging.log"
###############
#### RULES ####
###############
#
# First some standard log files. Log by facility.
#
auth,authpriv.* /var/log/auth.log
*.*;auth,authpriv.none -/var/log/syslog
#cron.* /var/log/cron.log
daemon.* -/var/log/daemon.log
kern.* -/var/log/kern.log
lpr.* -/var/log/lpr.log
mail.* -/var/log/mail.log
user.* -/var/log/user.log
local7.* -/var/log/cisco.log #all logs will go into the next file
*.* ?Incoming-logs #1 log per IP address
#
# Logging for the mail system. Split it up so that
# it is easy to write scripts to parse these files.
#
mail.info -/var/log/mail.info
mail.warn -/var/log/mail.warn
mail.err /var/log/mail.err
#
# Some "catch-all" log files.
#
*.=debug;\
auth,authpriv.none;\
news.none;mail.none -/var/log/debug
*.=info;*.=notice;*.=warn;\
auth,authpriv.none;\
cron,daemon.none;\
mail,news.none -/var/log/messages
#
# Emergencies are sent to everybody logged in.
#
*.emerg :omusrmsg:*- Restart the rsyslog service:
root@host:~# systemctl restart rsyslog.serviceLogs
- After a few seconds, the logs should appear:
root@host:~# cat /var/log/cisco.log
Dec 25 16:25:03 10.0.0.2 %PNPAGENT-I-PNPSRVRDETECT: PnP Server devicehelper.cisco.com was detected
Dec 25 16:25:06 10.0.0.2 %PNPAGENT-I-RESPSUCCESS: PnP Response Success
Dec 25 16:25:22 10.0.0.2 %PNPAGENT-I-PNPSRVRDETECT: PnP Server devicehelper.cisco.com was detected
Dec 25 16:25:23 10.0.0.1 %PNPAGENT-I-PNPSRVRDETECT: PnP Server devicehelper.cisco.com was detectedroot@host:~# cat /var/log/10.0.0.1/logging.log
Dec 25 16:25:23 10.0.0.1 %PNPAGENT-I-PNPSRVRDETECT: PnP Server devicehelper.cisco.com was detected