Here's a how to about setting up a OpenVPN server under Debian 10 Buster.
root@host:~# apt install openvpn
root@host:~# cd /etc/openvpn/
root@host:~# sed -i 's/#AUTOSTART="all"/AUTOSTART="all"/' /etc/default/openvpn
I had « read UDP: Unknown error (code=10054) » and « TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) » error on the client side. The reason seems to be that the default OpenVPN systemd file is broken. If you have the same message, enable the openvpn@.service.
root@host:~# systemctl enable openvpn@.service
root@host:~# /usr/share/easy-rsa/easyrsa clean-all
root@host:~# /usr/share/easy-rsa/easyrsa init-pki
WARNING!!!
You are about to remove the EASYRSA_PKI at: /etc/openvpn/pki
and initialize a fresh PKI here.
Type the word 'yes' to continue, or any other input to abort.
Confirm removal: yes
root@host:~# /usr/share/easy-rsa/easyrsa build-ca nopass
Using SSL: openssl OpenSSL 1.1.1d 10 Sep 2019 Generating RSA private key, 2048 bit long modulus (2 primes) ...+++++ ...........+++++ e is 65537 (0x010001) Can't load /etc/openvpn/pki/.rnd into RNG 139967504692352:error:2406F079:random number generator:RAND_load_file:Cannot open file:../crypto/rand/randfile.c:98:Filename=/etc/openvpn/pki/.rnd You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [Easy-RSA CA]:openvpn-host CA creation complete and you may now import and sign cert requests. Your new CA certificate file for publishing is at: /etc/openvpn/pki/ca.crt
root@host:~# /usr/share/easy-rsa/easyrsa build-server-full server nopass
root@host:~# /usr/share/easy-rsa/easyrsa gen-dh
Client certificates are inside /etc/openvpn/pki/private/ and /etc/openvpn/pki/issued/ directories.
root@host:~# /usr/share/easy-rsa/easyrsa build-client-full client01 nopass
root@host:~# for i in $(seq -w 1 10);do /usr/share/easy-rsa/easyrsa build-client-full client"$i" nopass; done
port 1194 proto udp dev tun ca /etc/openvpn/pki/ca.crt # generated keys cert /etc/openvpn/pki/issued/server.crt key /etc/openvpn/pki/private/server.key # keep secret dh /etc/openvpn/pki/dh.pem server 10.50.8.0 255.255.255.0 # internal tun0 connection IP ifconfig-pool-persist ipp.txt keepalive 10 120 comp-lzo # Compression - must be turned on at both end persist-key persist-tun push "dhcp-option DNS 192.168.0.200" push "dhcp-option DOMAIN std.local" push "route 192.168.0.0 255.255.255.0" status /var/log/openvpn-status.log verb 3 # verbose mode
root@host:~# systemctl restart openvpn.service
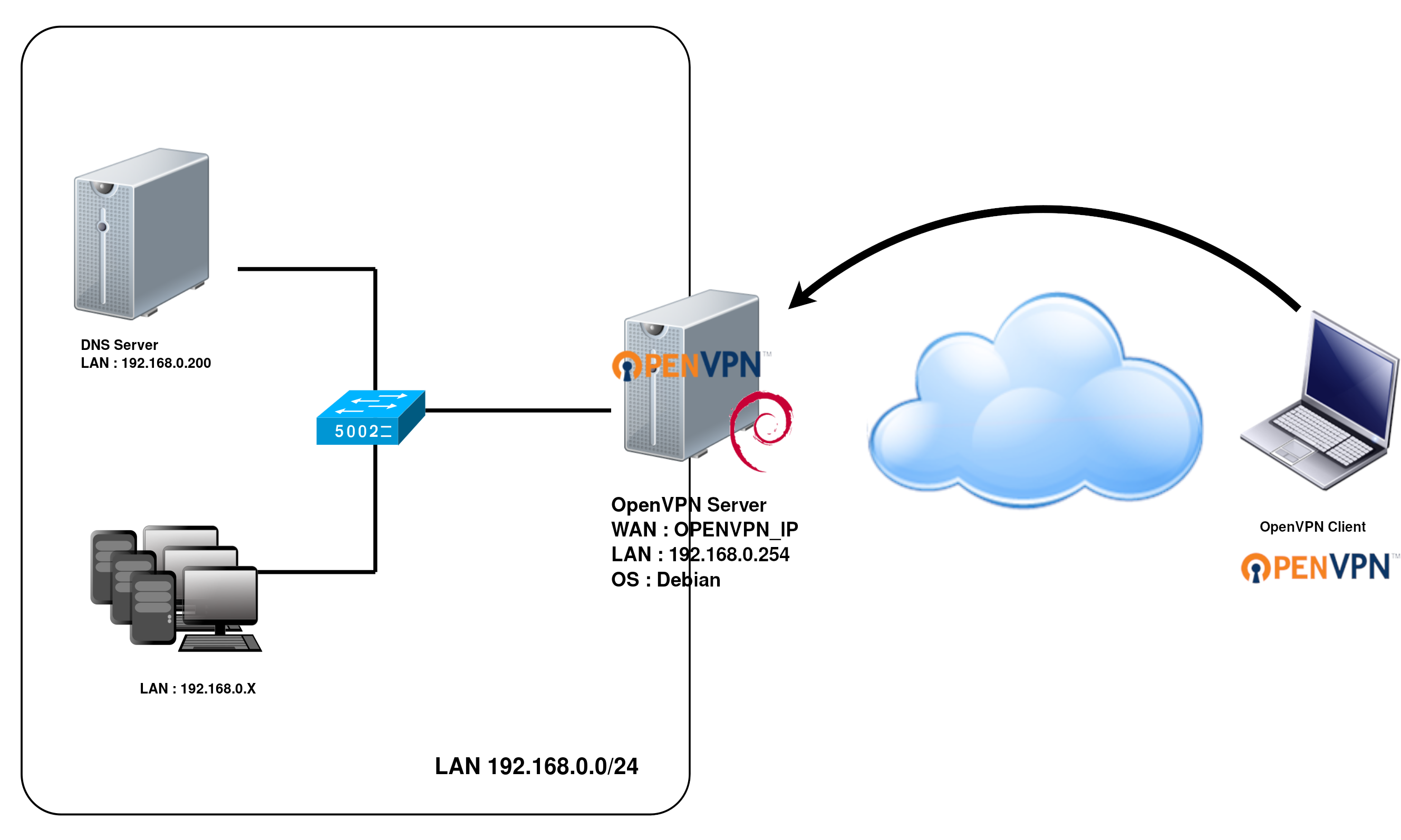
Router mode will allow us to make the 192.168.0.0/24 network reachable from the client side.
A simple netfilter rule to allow vpn clients to access to the entire network :
root@host:~# ip addr sh
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens192: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 01:02:a0:21:fd:54 brd ff:ff:ff:ff:ff:ff
inet OPENVPN_IP brd X.X.X.X scope global wan
valid_lft forever preferred_lft forever
inet6 fe80::ff:fe5d:f333/64 scope link
valid_lft forever preferred_lft forever
3: enp2s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 11:a2:a9:21:fd:54 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.254 brd X.X.X.X scope global wan
valid_lft forever preferred_lft forever
inet6 fe80::6a05:caff:fe39:c153/64 scope link
valid_lft forever preferred_lft forever
root@host:~# iptables -t nat -A POSTROUTING -s 10.50.8.0/24 -o enp2s0 -j MASQUERADE
net.ipv4.ip_forward=1
root@host:~# sysctl -p /etc/sysctl.conf
client
dev tun
proto udp
remote OPENVPN_IP 1194
resolv-retry infinite
nobind
persist-key
persist-tun
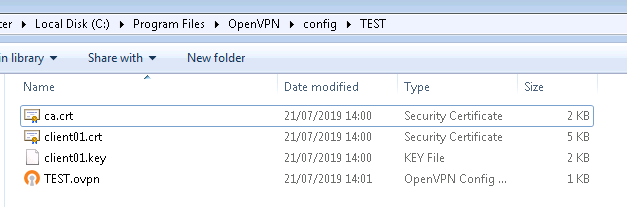
ca ca.crt
cert client01.crt
key client01.key
comp-lzo
verb 3
Contact :