Retrieve Windows Version of Computers in a Domain
- Last updated: Jan 20, 2025

Intro
Initially, it was possible from the WSUS console to find out the Windows version of managed computers, but since Windows 10 this no longer works as well. Or rather, it doesn't work at all.
So I've been working on a PowerShell script to get the exact version of computers in a domain.
The aim of this article is to extract a list of computers with their Windows versions into a csv file.
Update: I first found a solution based on WinRM, but finally opted for an even simpler solution that uses the Get-ADComputer command. I'm leaving the WinRM option as it can be used for other purposes.With the Get-ADComputer command (New)
- Retrieve the Windows version of all computers and export the information to a csv file
C:\OS_Version_List.csv:
PS C:\ > Get-ADComputer -Filter '*' -Property * | Select-Object Name,OperatingSystem,OperatingSystemVersion | Export-Csv -Path C:\OS_Version_List.csv- Displays the Windows version for all enabled computers:
PS C:\ > Get-ADComputer -Filter {(Enabled -eq $True)} -Property * | Select-Object Name,OperatingSystem,OperatingSystemVersion -Wrap -Autosize- Displays the Windows version for all enabled computers whose name starts with PC0 and whose operating system name starts with Windows 7:
PS C:\ > Get-ADComputer -Filter 'Name -Like "PC0*" -and Enabled -eq $True' -Property * | Where-Object { $_.OperatingSystem -like "Windows 7*" } | Select-Object Name,OperatingSystem,OperatingSystemVersion -Wrap -Autosize- Show the Windows version for all enabled computers that have been connected for up to 120 days and whose name starts with PC0:
PS C:\ > Get-ADComputer -Filter {(Enabled -eq $True) -and (Name -Like "PC0*")} -Properties * | where { ($(Get-Date)-[DateTime]::FromFileTime($_.LastLogonTimeStamp)).Days -lt 120 } | Select-object Name,OperatingSystem,OperatingSystemVersionWinRM method (Old)
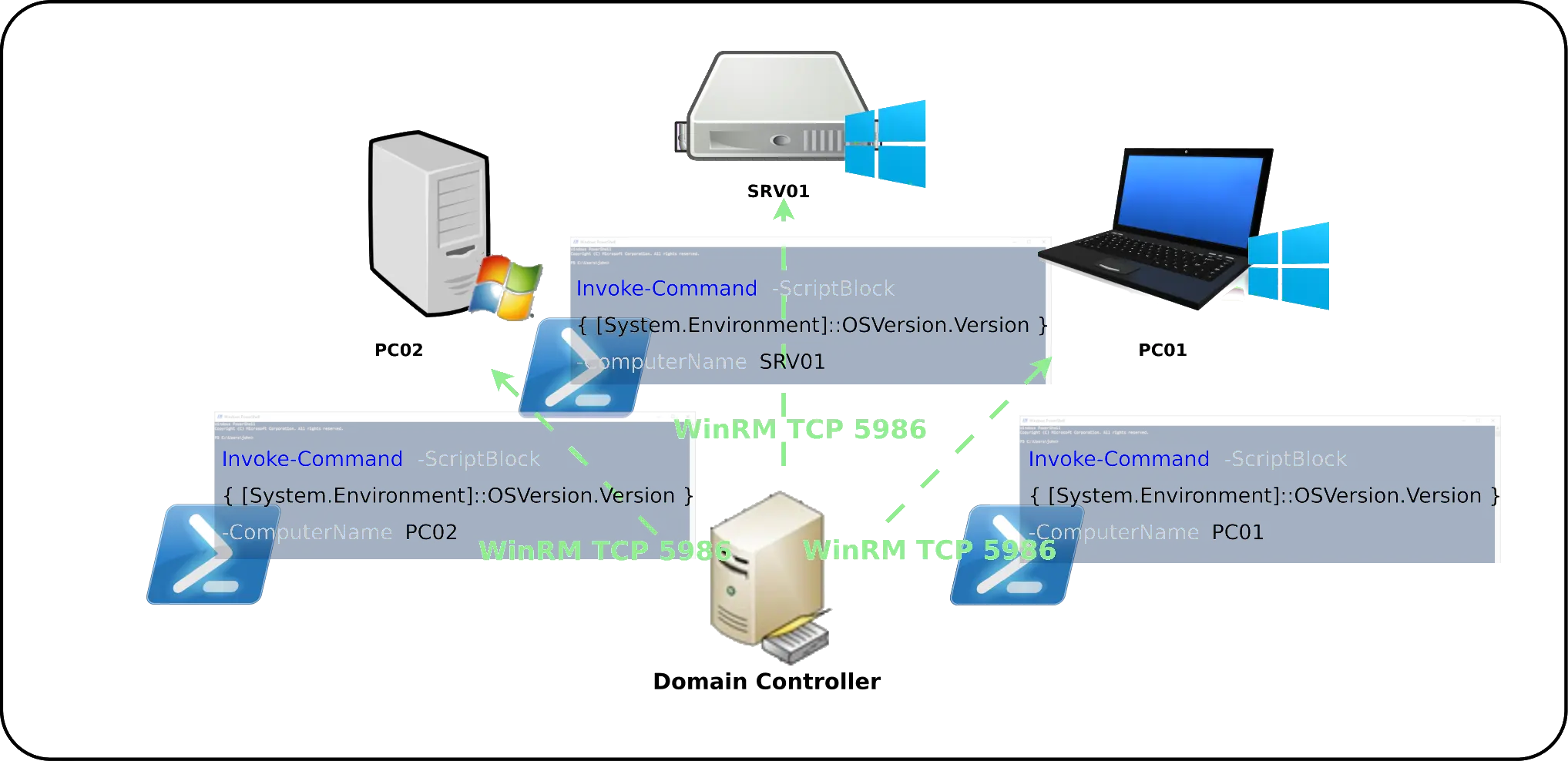
Here, I'll be using Windows Remote Management, so we need to enable it on every computer we want to retrieve the OS version, for which we can do so via GPO.
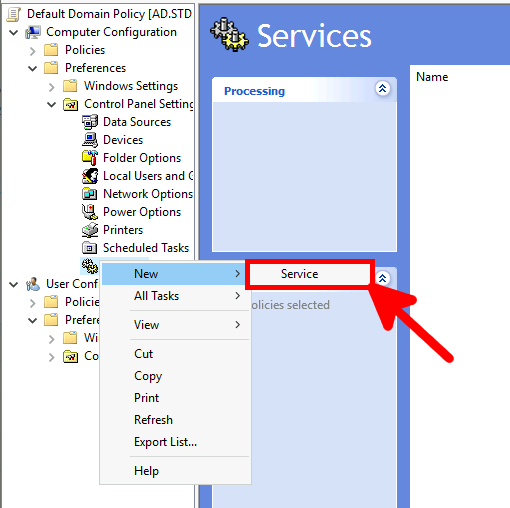
Activate WinRM with a GPO
- In your GPO, go to Computer Configuration > Preferences > Control Panel Settings > Services and create a new service:
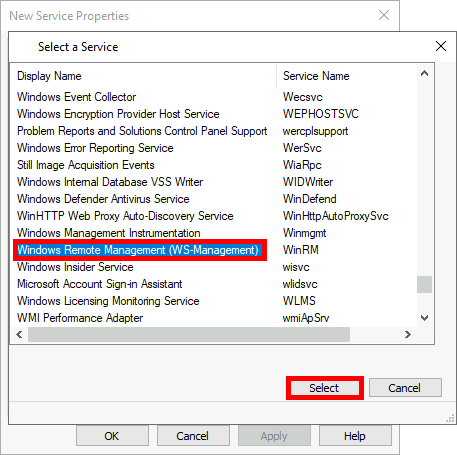
- Select Windows Remote Management (WS-Management) and click on Select:
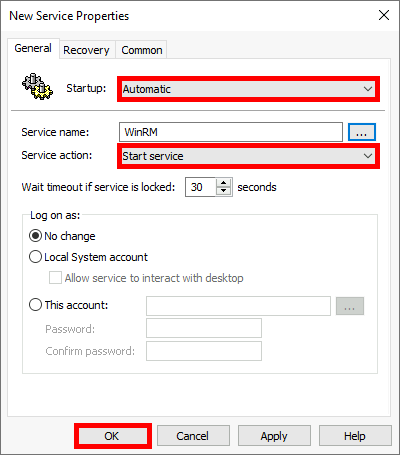
- Set the parameters and click OK:
- Go to Computer configuration > Policies > Administrative Templates > Windows Components > Windows Remote Management (WinRM) > WinRM Service and edit the Allow remote server management through WinRM rule:
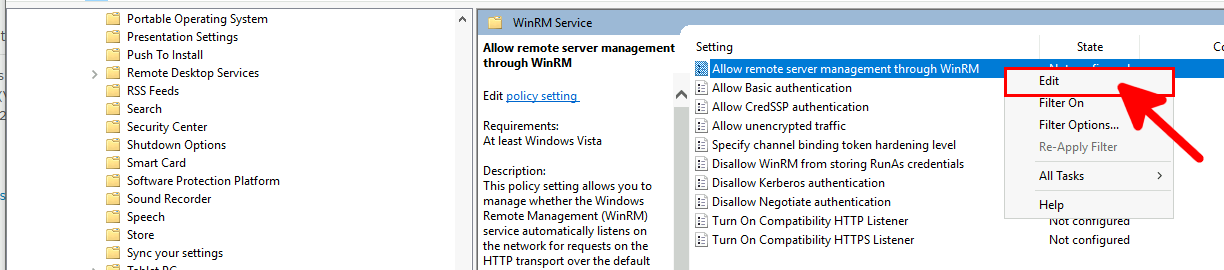
- Enable and define the rule, then click OK:
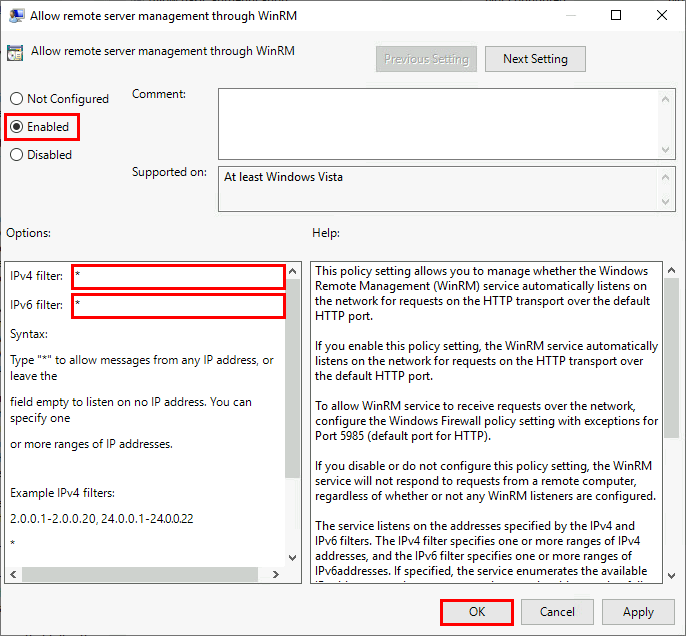
Allow WinRM on the firewall
WinRM uses TCP ports 5985 (HTTP) or 5986 (HTTPS), so these ports must be open on the target firewall.
Normally, in an Active Directory environment, unencrypted connections (5985 (HTTP)) are disabled. You can check this with the following command:
PS C:\ > winrm get winrm/config/serviceCheck WinRM connectivity
- Check WinRM service status (on source and destination hosts):
PS C:\ > (Get-Service WinRM).Status- From a Domain Controller, run this command to see if we can retrieve the operating system version, example here with PC01:
PS C:\ > Invoke-Command -ScriptBlock { [System.Environment]::OSVersion.Version } -ComputerName PC01 | Select-Object PSComputerName,Build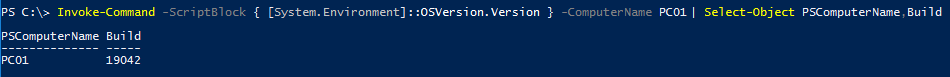
Script to csv
I've written a little script that tests wether the computers (from PC0001 to PC0400) are reachable, if so it tries to retrieve the operating system version via WinRM and writes the information to a C:\OS_Version_List.csv file.
#Test for PC0001 to PC0400
1..400 | foreach {
$i="{0:D4}" -f $_
$ping = ping -n 1 "PC$i"| findstr "TTL"
if ($LASTEXITCODE -eq "0")
{
$ip = $PING -replace ".* ([0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}).*",'$1'
Write-Host "PC$i is up"
Try { Invoke-Command -ScriptBlock { [System.Environment]::OSVersion.Version } -ComputerName "PC$i" -ErrorAction Stop | Select-Object PSComputerName,Build,@{Name="IP";Expression={"$ip"}} | Export-Csv -Path C:\OS_Version_List.csv -Append }
Catch { '' | Select-Object @{Name="PSComputerName"; Expression={"PC$i"}},@{Name="Build"; Expression={"UNKNOWN"}},@{Name="IP";Expression={"$ip"}} | Export-Csv -Path C:\OS_Version_List.csv -Append }
} else {
Write-Host "PC$i is not available"
}
}