Obtain and Configure SSL Certificates for Linux Web Servers in an AD CS Environment
- Last updated: Nov 2, 2024
In this article I'll show you how to set up SSL certificates for a GNU/Linux web server in an AD CS environment. The aim is to have web servers available on the corporate network secured by SSL but without the warning that can be encountered with self-signed certificates.
I'll be using a Debian machine with an Apache HTTP Server, but this can be reproduced on any distribution and any web server.
Generating a Certificate Signing Request (CSR)
- From the Debian server, create an
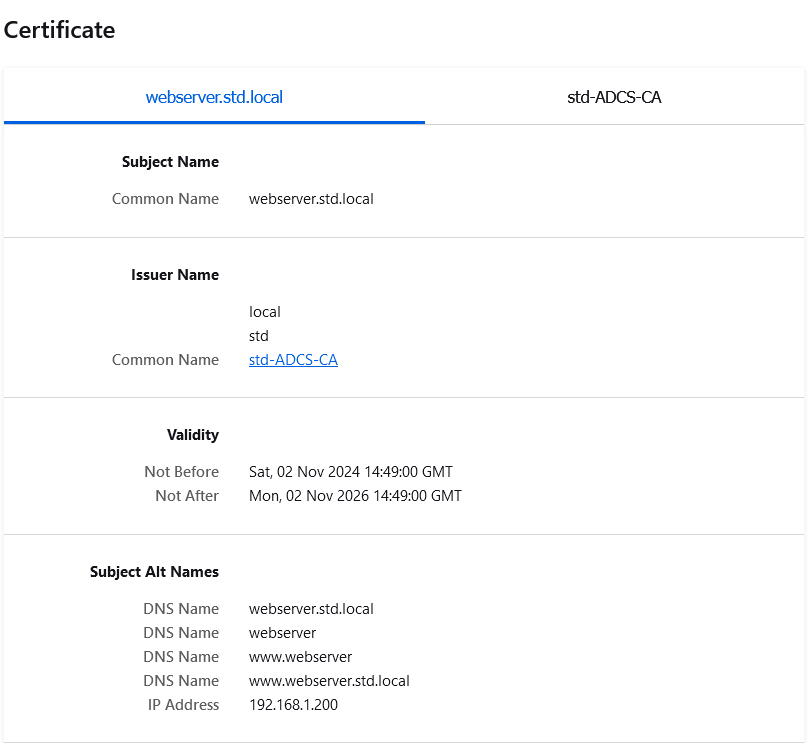
openssl-san.cnffile, example here with a web server namedwebserver.std.localwhich has the following IP address:192.168.1.200. Note the different alternative names, corresponding to the different urls that users can use to access the website:
[ req ]
default_bits = 4096
prompt = no
default_md = sha512
distinguished_name = dn
req_extensions = req_ext
[ dn ]
CN = webserver.std.local
[ req_ext ]
subjectAltName = @alt_names
[ alt_names ]
DNS.1 = webserver.std.local
DNS.2 = webserver
DNS.3 = www.webserver
DNS.4 = www.webserver.std.local
IP.1 = 192.168.1.200- Next, use the
opensslcommand to generate a private key and a certificate signing request for our ADCS:
user@webserver:~$ openssl req -new -nodes -keyout webserver.std.local.key -out webserver.std.local.csr -config openssl-san.cnf- Copy the
csrfile to/tmp/for later retrieval from the AD CS server:
user@webserver:~$ cp webserver.std.local.csr /tmp/Requesting a Certificate from Windows AD CS
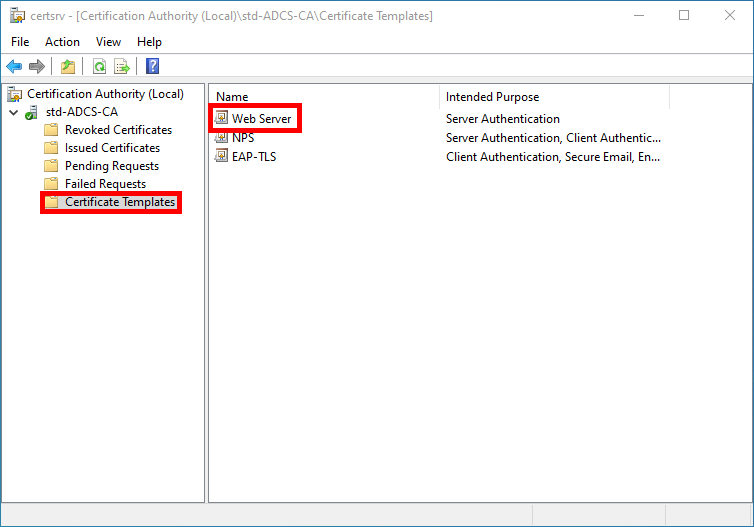
- From the AD CS server, open the Certificate Templates Settings console, and make sure you have the Web Server template:
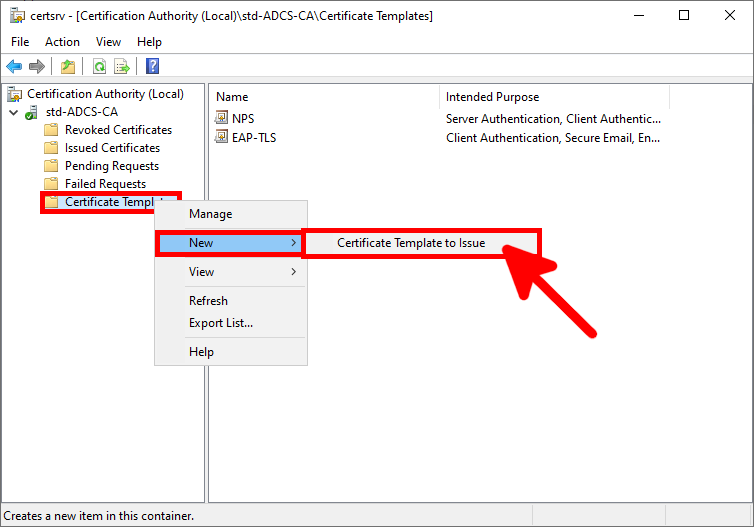
- If not, right-click on Certificate Templates and click on Certificate Template to Issue:
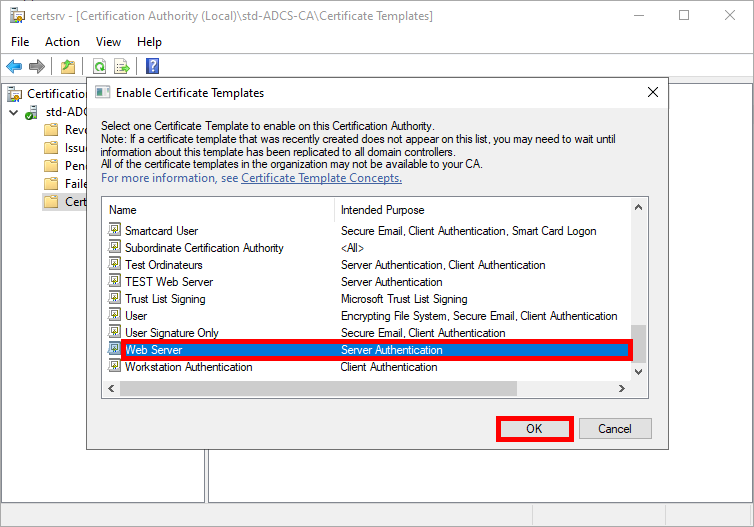
- Select the Web Server template, and click on OK:
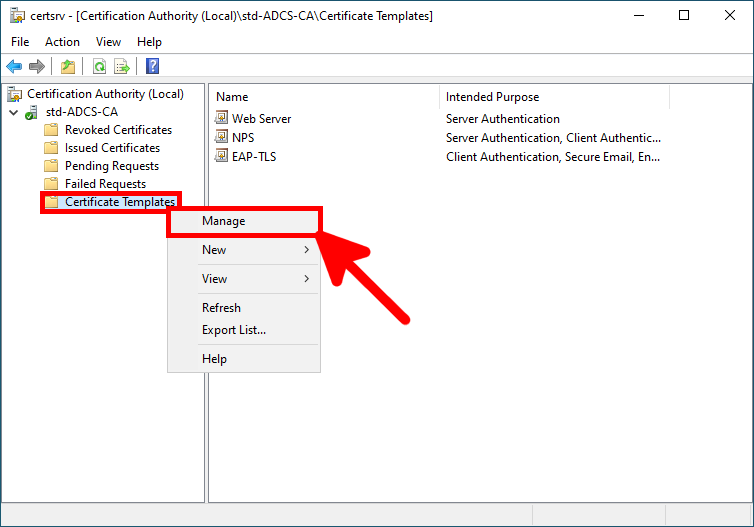
- Now right-click on Certificate Templates, and click on Manage:
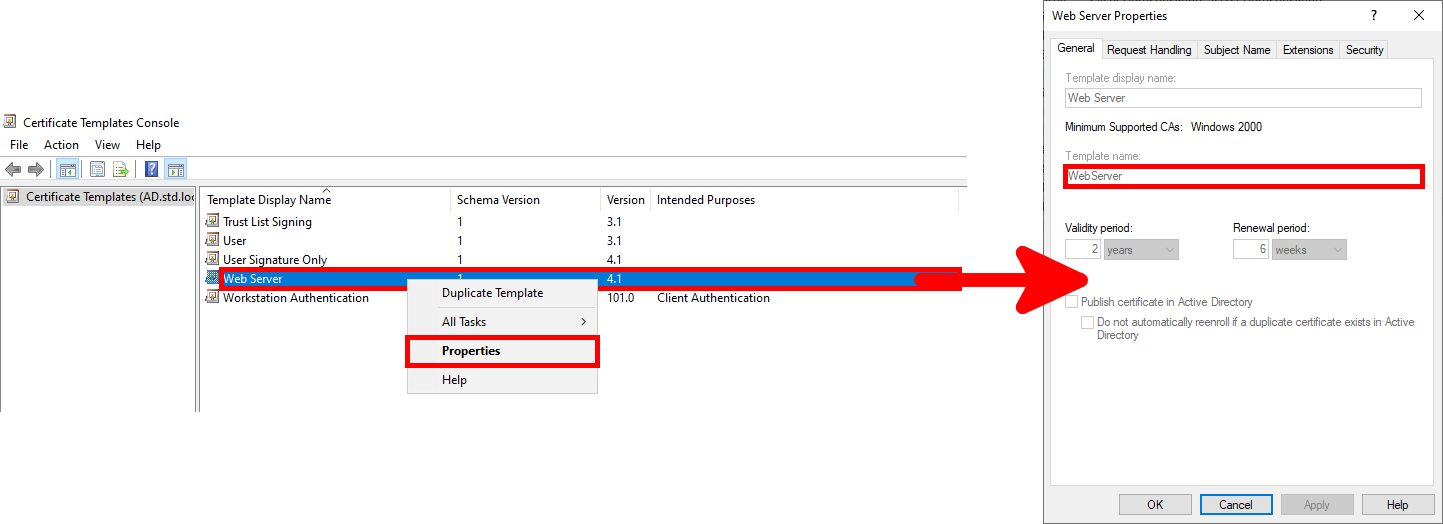
- In the Certificate Templates console, right-click on Web Server, and note the name of the template, which will be used later with the
certreqcommand:
- Copy the certificate signing request file from the web server, for example here with a PowerShell command:
PS > scp user@192.168.1.200:/tmp/webserver.std.local.csr .- From a PowerShell console, request a certificate to the AD CS certification authority:
PS > certreq -submit -attrib "CertificateTemplate:webserver" .\webserver.std.local.csr webserver.std.local.cer- A Certification Authority List window should appear, click on OK:
- If everything goes well, the Issued message should appear indicating that the certificate has been issued in the current directory:
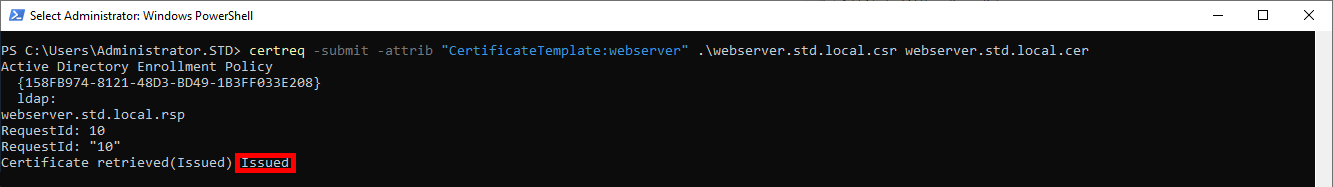
- Copy the
cercertificate to the Linux Web Server, for example here with a PowerShell command that copies it to the web server's/tmpdirectory:
PS > scp webserver.std.local.cer user@192.168.1.200:/tmp/Installing the Issued Certificate on an Apache Web Server
- Connect to your Linux web server and copy the SSL certificates into these folders (note that the
cerfile has been renamed topem):
root@webserver:~# cp /tmp/webserver.std.local.cer /etc/ssl/certs/webserver.std.local.pemroot@webserver:~# cp /home/user/webserver.std.local.key /etc/ssl/private/webserver.std.local.key- Edit the configuration file of your https Apache2 site, for example here the file
/etc/apache2/sites-enabled/default-ssl.conf:
# A self-signed (snakeoil) certificate can be created by installing
# the ssl-cert package. See
# /usr/share/doc/apache2/README.Debian.gz for more info.
# If both key and certificate are stored in the same file, only the
# SSLCertificateFile directive is needed.
SSLCertificateFile /etc/ssl/certs/webserver.std.local.pem
SSLCertificateKeyFile /etc/ssl/private/webserver.std.local.key- Reload the Apache2 service:
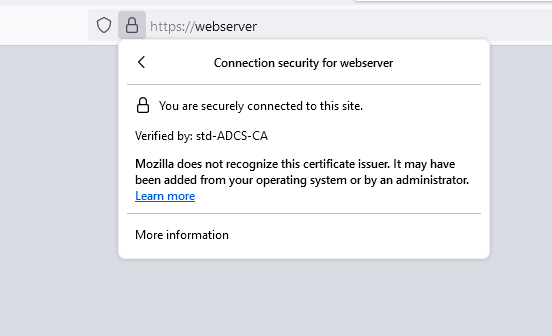
root@webserver:~# systemctl reload apache2.service- From a machine in the domain, open a web browser and connect to the web server url (https://webserver for example). You should no longer see the warning. From the web browser, you can check the certificate properties: