How to harden the Windows Operating Systems
- Last updated: Jun 27, 2024
I will put here all the actions I take to secure Microsoft Windows operating systems. I hope it will be useful to you! :)
This guide can be used independently on workstations or servers.
BIOS
- Here a list of actions that I set up :
- Update BIOS firmware to latest
- Enable secure boot
- Set BIOS password to prevent unwanted changes
- Disable booting on USB or any other external device
Users Accounts
For most uses cases we do not need to work under an administrator session. The latter should only be used for specific cases (softwares installations, modification of the Windows configuration etc…). So the first thing to do is to create a user session without administrator rights.
- From an administrator command create standard account :
net user stduser 1userP@SSWORD /add
- From an administrator command create administrator account :
net user adminuser 1admin@SSWORD /add
net localgroup administrators adminuser /add
Services
In order to reduce the attack surface it is important to disable services that we don't use.
| Service | Service Name | Comment |
|---|---|---|
| AllJoyn Router Service | AJRouter | |
| Bluetooth Support Service | bthserv | |
| Connected User Experiences and Telemetry | DiagTrack | |
| Device Management Wireless Application Protocol (WAP) Push message Routing Service | dmwapphushservice | |
| Function Discovery Provider Host | fdPHost | |
| Function Discovery Resource Publication | FDResPub | |
| Geolocation Service | lfsvc | |
| Link-Layer Topology Discovery Mapper | lltdsvc | |
| Network Connected Devices Auto-Setup | NcdAutoSetup | |
| Peer Networking Identity Manager | p2pimsvc | |
| Peer Networking Grouping | p2psvc | |
| Peer Name Resolution Protocol | PNRPsvc | |
| Remote Access Auto Connection Manager | RasAuto | |
| Remote Access Connection Manager | RasMan | |
| Routing and Remote Access | RemoteAccess | |
| Remote Registry | RemoteRegistry | |
| Retail Demo Service | retaildemo | |
| Internet Connection Sharing (ICS) | SharedAccess | |
| SSDP Discovery | SSDPSRV | |
| UPnP Device Host | upnphost | |
| Windows Connect Now - Config Registrar | wcncsvc | |
| WLAN AutoConfig | WlanSvc | |
| Microsoft Account Sign-in Assistant | wlidsvc | |
| Windows Media Player Network Sharing Service | WMPNetworkSvc | |
| WWAN AutoConfig | WwanSvc | |
| Xbox Live Auth Manager | XblAuthManager | |
| Xbox Live Game Save | XblGameSave | |
| Xbox Accessory Management Service | XboxGipSvc | |
| Xbox Live Networking Service | XboxNetApiSvc |
- Script to disable services :
sc.exe config AJRouter start=disabled
sc.exe config bthserv start=disabled
sc.exe config DiagTrack start=disabled
sc.exe config dmwappushservice start=disabled
sc.exe config fdPHost start=disabled
sc.exe config FDResPub start=disabled
sc.exe config lfsvc start=disabled
sc.exe config lltdsvc start=disabled
sc.exe config NcdAutoSetup start=disabled
sc.exe config p2pimsvc start=disabled
sc.exe config p2psvc start=disabled
sc.exe config PNRPsvc start=disabled
sc.exe config RasAuto start=disabled
sc.exe config RasMan start=disabled
sc.exe config RemoteAccess start=disabled
sc.exe config RemoteRegistry start=disabled
sc.exe config retaildemo start=disabled
sc.exe config SharedAccess start=disabled
sc.exe config SSDPSRV start=disabled
sc.exe config upnphost start=disabled
sc.exe config wcncsvc start=disabled
sc.exe config WlanSvc start=disabled
sc.exe config wlidsvc start=disabled
sc.exe config WMPNetworkSvc start=disabled
sc.exe config WwanSvc start=disabled
sc.exe config XblAuthManager start=disabled
sc.exe config XblGameSave start=disabled
sc.exe config XboxGipSvc start=disabled
sc.exe config XboxNetApiSvc start=disabled
Windows Firewall
Set default actions

We can use the Windows Firewall to allow only the network flows needed.
To do so, we will deny input and output by defaults.
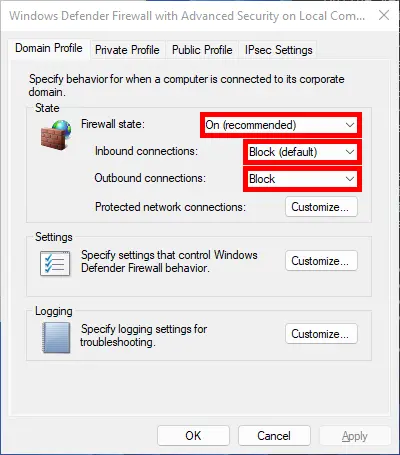
- Enable Windows Firewall and block inbound and outbound traffic :
PS C:\Windows\system32> Set-NetFirewallProfile -Profile Domain,Public,Private -DefaultInboundAction Block -DefaultOutboundAction Block -Enabled True
- You can do the same with the graphical mmc :
Troubleshoot
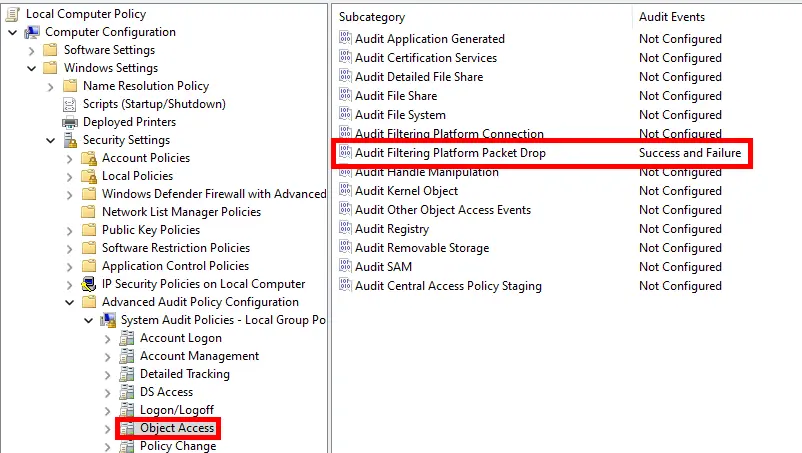
With theses restrictives rules legit traffic could be blocked. To track the traffic which is blocked we will have to enable firewall log.
- Edit group policy and enable the Audit Filtering Platform Packet Drop :
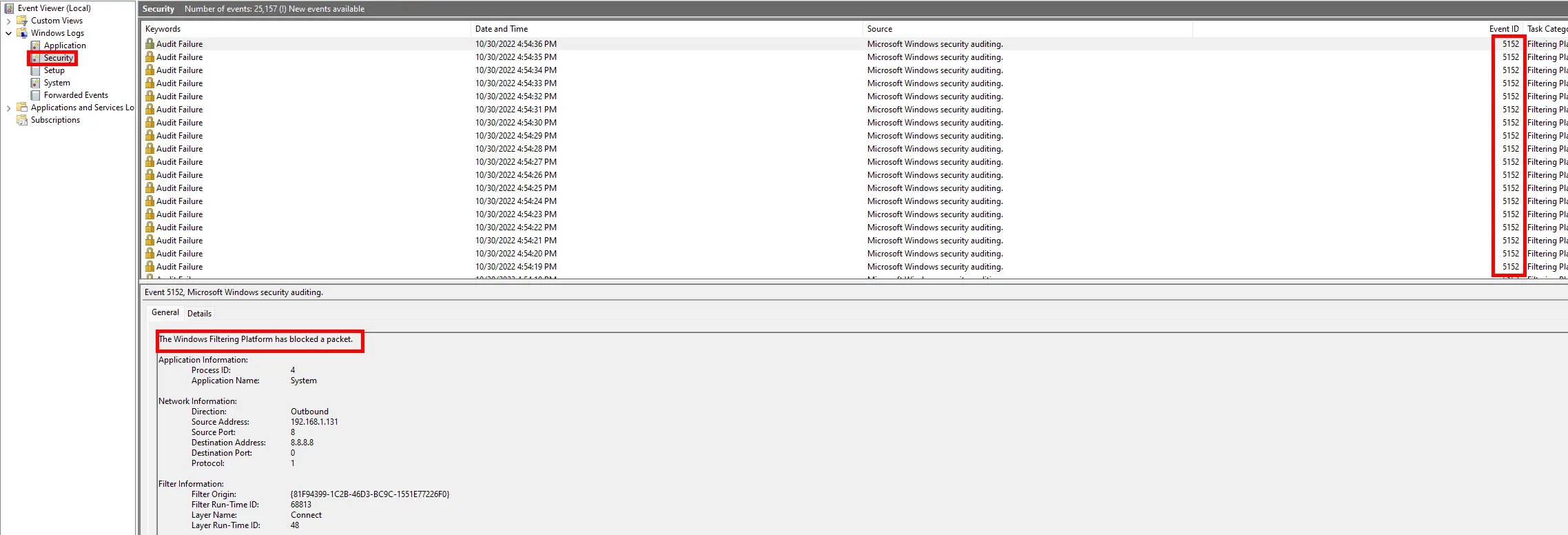
- Then open Windows Event Viewer to see blocked traffic (event id : 5152) :
Windows Update
Microsoft published security update very often, so update your system via Windows Update as soon as you can.
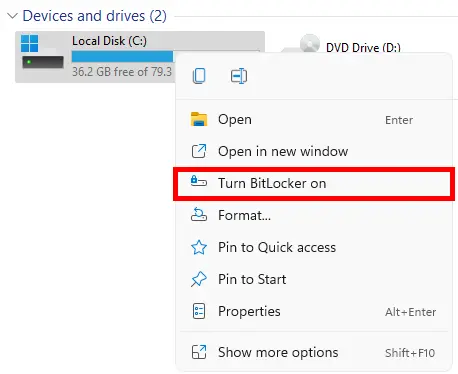
Encrypt the hard drive
Especially on the laptops, encrypting the hard drive is a very good security feature to harden the system. We can use BitLocker or any others solution (As VeraCrypt for example).
Windows Optional Feature
Some older Windows Features are still enabled in recent versions of Windows. We will see here how to disable them with PowerShell.
- SMB is the sharing protocol in the Windows environment. SMB 1.0 is obsolete and weak from a security point of view. It should therefore be disabled:
PS C:\Windows\system32> Disable-WindowsOptionalFeature -FeatureName "SMB1Protocol" -Online
- On some versions of Windows, Windows PowerShell v2.0 is enabled by default. This version is obsolete and can be disabled:
PS C:\Windows\system32> Disable-WindowsOptionalFeature -FeatureName "MicrosoftWindowsPowerShellV2" -Online
- If not used, we can also disable the Fax Services Client:
PS C:\Windows\system32> Disable-WindowsOptionalFeature -FeatureName "FaxServicesClientPackage" -Online
Group Policy
There are a lot of parameters inside group policy to harden the system.
| Group Policy | Value | Comment |
|---|---|---|
| Computer Configuration > Windows Settings > Security Settings > Account Policies > Password Policy | ||
| Enforce password history | 24 | |
| Maximum password age | 90 | |
| Minimum password age | 1 | |
| Password must meet complexity requirements | Enabled | |
| Minimum password lenght | 10 | |
| Store password using reversible encryption | Disabled | |
| Computer Configuration > Windows Settings > Security Settings > Account Policies > Account Lock Policy | ||
| Account lockout threshold | 10 | |
| Account lockout duration | 5 minutes | |
| Reset account lockout counter after | 5 minutes | |
| Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment | ||
| Access this computer from the network | Administrators, Authenticated Users | |
| Allow log on through Remote Desktop Services | - | Add accounts which are authorized to use RDS |
| Deny access to this computer from the network | DefaultGuest | Add Local Account if in a domain |
| Deny log on locally | Defaultguest | Add domain administrators if in a domain |
| Deny log on as a service | Defaultguest | Add domain administrators if in a domain |
| Deny log on as a batch job | DefaultGuest | Add domain administrators if in a domain |
| Deny log on through Remote Desktop Services | DefaultGuest | Add domain administrators and Local Account if in a domain |
| Allow log on locally | Administrators and Authenticated Users | |
| Increase scheduling priority | Administrators | |
| Restore files and directories | Administrators | |
| Back up files and directories | Administrators | |