How to Synchronize Active Directory User Accounts to EntraID with Microsoft Entra Connect
- Last updated: Oct 26, 2024
We may regret it (at least I do), but Entra ID is increasingly used in enterprises as Microsoft's cloud solution for user account management. It serves as the user account database for all Microsoft cloud services such as Microsoft Azure and Microsoft 365 to authenticate users. Since many organizations still rely on local Active Directory (AD on-premise), it can be very advantageous to synchronize user accounts from on-premise AD to Entra ID. This synchronization offers several advantages, including streamlined account management—administrators only need to create the account once—and password synchronization.
To enable this synchronization, Microsoft provides a tool called Microsoft Entra Connect (previously known as Azure Connect; staying up to date with Microsoft's naming conventions can be as difficult as staying up to date with this site's CSS changes…).
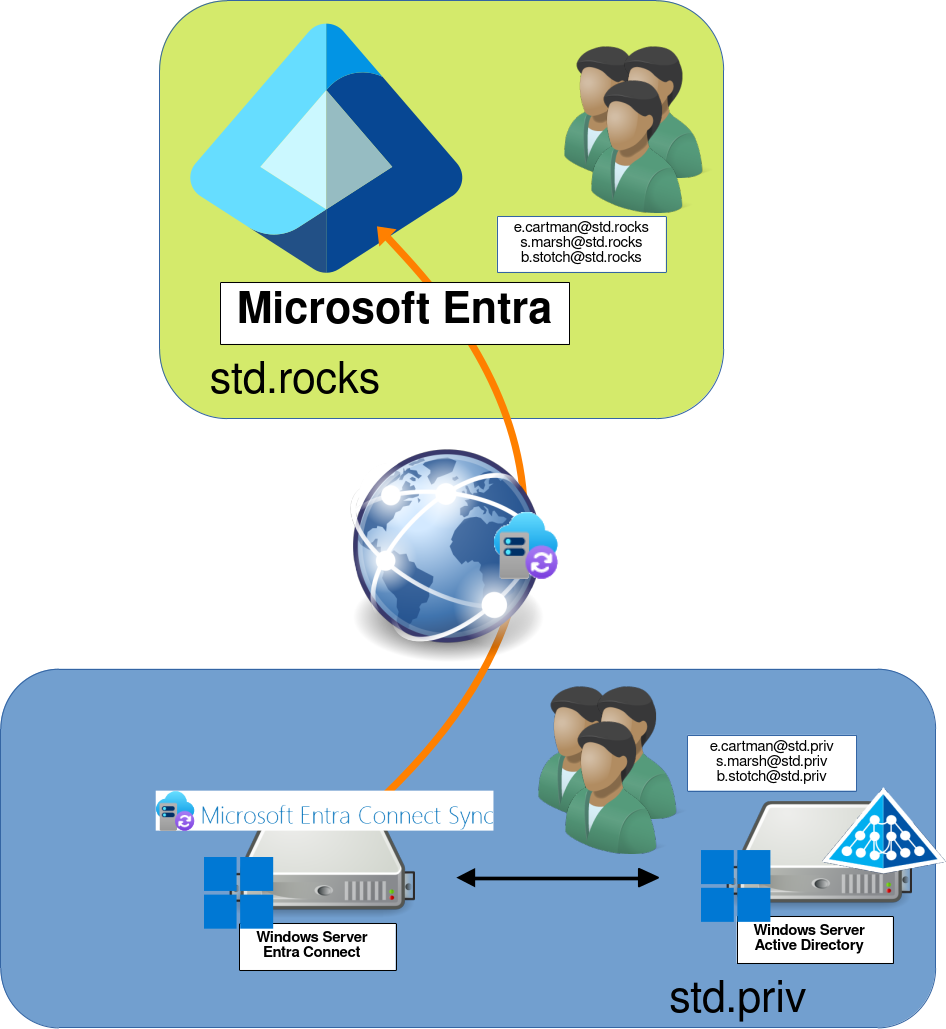
- Details of the test architecture:
- Local domain: std.priv
- Entra domain: std.rocks
Network Diagram
Prerequisites
- Prerequisites:
- .Net: 4.7.2
- Tls: 1.2
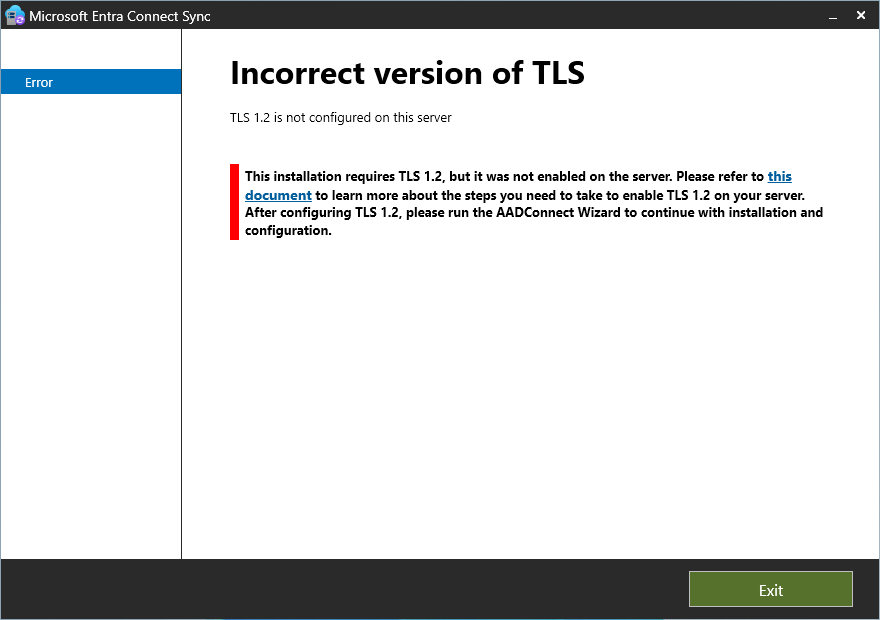
Make sure you have a version of .Net at least equal to 4.7.2 and Tls with version 1.2. For example, on a Windows 2016 server, I had to update my .Net version and activate Tls to 1.2.
- Below is the error message: Incorrect version of Tls when lauching Entra Connect for the first time:
- To solve this problem, first display the currently configured Tls version (Note: on Windows Server 2025, it only returns: SystemDefault, which isn't very useful…):
PS C:\> [Net.ServicePointManager]::SecurityProtocol
Ssl3, Tls
- Run this PowerShell script to permanently activate Tls 1.2:
If (-Not (Test-Path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319'))
{
New-Item 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -Name 'SystemDefaultTlsVersions' -Value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -Name 'SchUseStrongCrypto' -Value '1' -PropertyType 'DWord' -Force | Out-Null
If (-Not (Test-Path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319'))
{
New-Item 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -Name 'SystemDefaultTlsVersions' -Value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -Name 'SchUseStrongCrypto' -Value '1' -PropertyType 'DWord' -Force | Out-Null
If (-Not (Test-Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server'))
{
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Name 'Enabled' -Value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Name 'DisabledByDefault' -Value '0' -PropertyType 'DWord' -Force | Out-Null
If (-Not (Test-Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client'))
{
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Name 'Enabled' -Value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Name 'DisabledByDefault' -Value '0' -PropertyType 'DWord' -Force | Out-Null
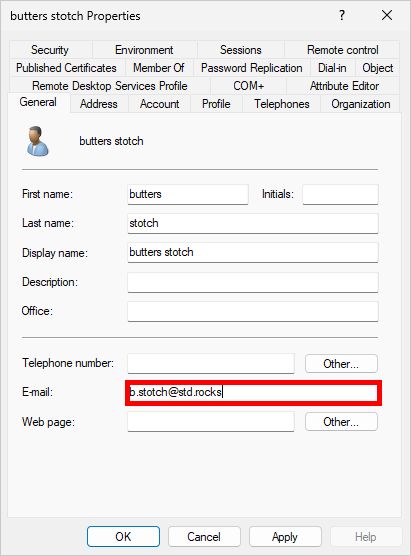
Another prerequisite in our configuration is to have the E-mail field filled in for the Active Directory user accounts that will be synchronized in Entra. I'm in a case where the local domain is private (std.priv) and therefore different from that of Entra-ID (std.rocks). It is therefore the E-mail field that will contain the link between the on-premise account and the one in Entra-ID.
Installing Microsoft Entra Connect
Download the latest version of Microsoft Entra Connect from the official Microsot website: https://www.microsoft.com/en-us/download/details.aspx?id=47594.
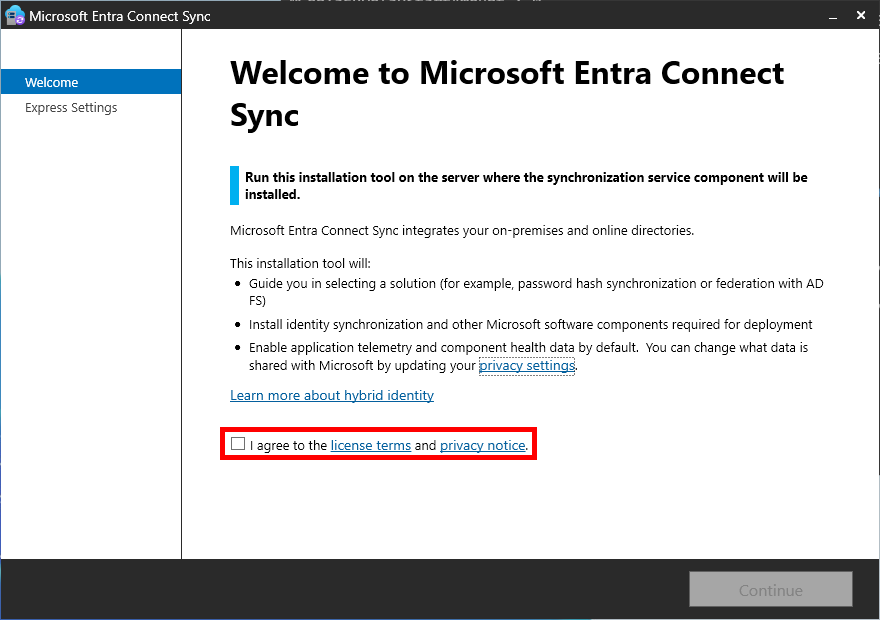
- Check the box I agree to the license… and click on Continue:
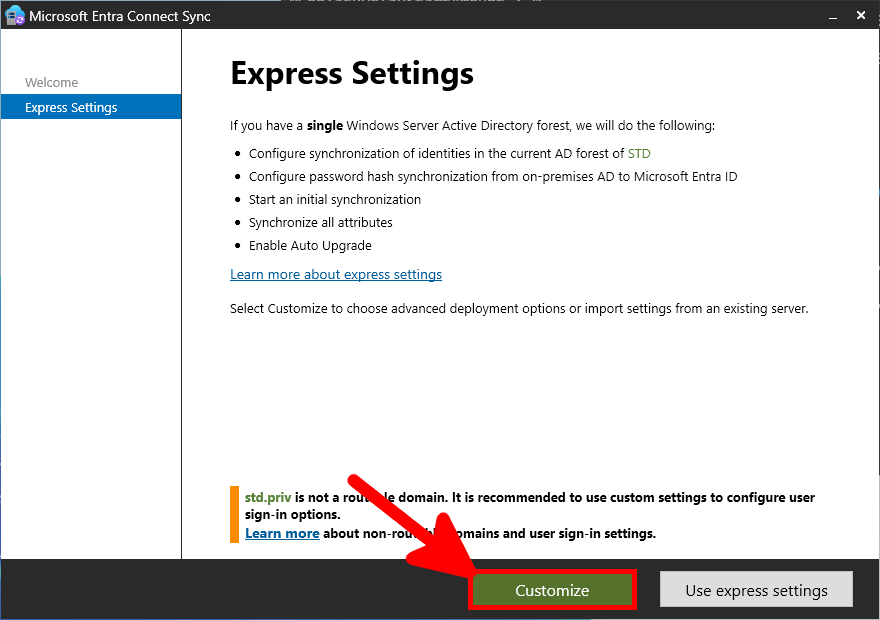
- On the Express Settings page, click on Customize:
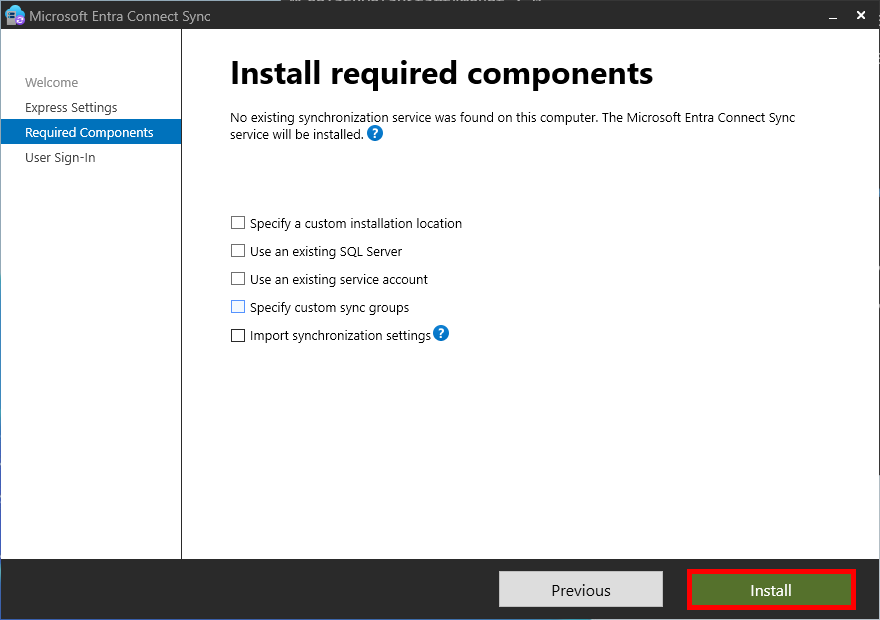
- On the Install required components page, click on Install:
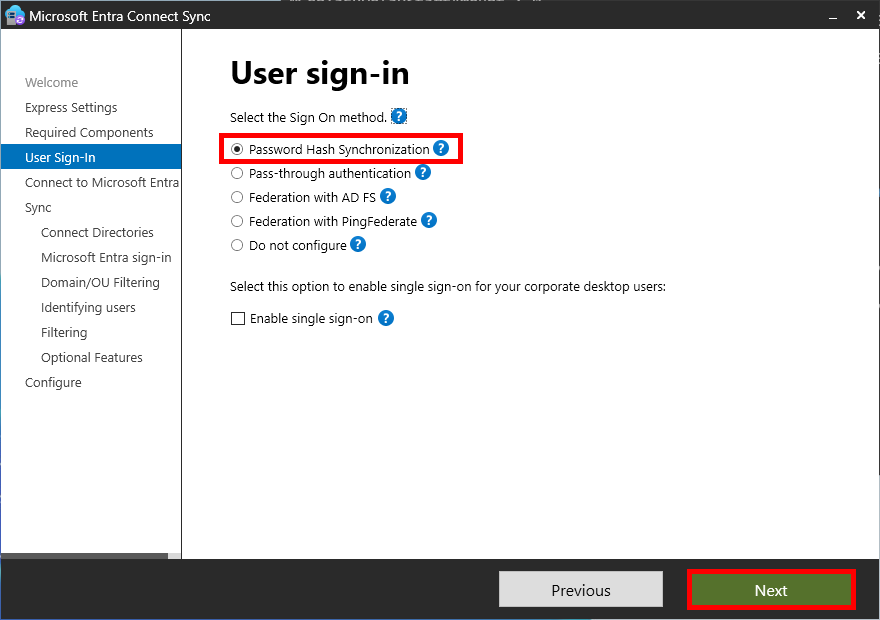
- On the User sign-in page, select Password Hash Synchronization, then click Next:
- On the Connect to Microsoft Entra ID page, enter a tenant administrator ID in the USERNAME box and click Next:
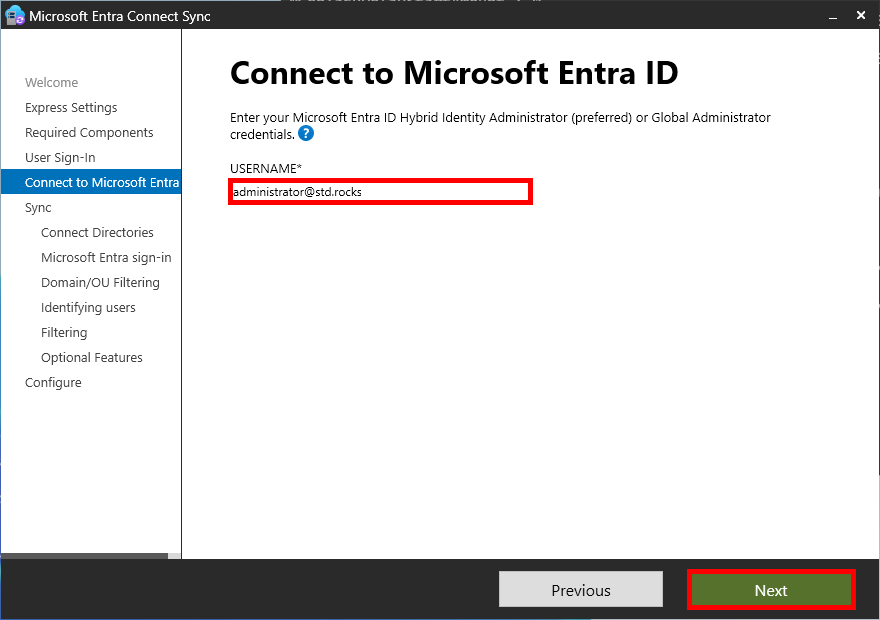
- Sign in with account credentials:
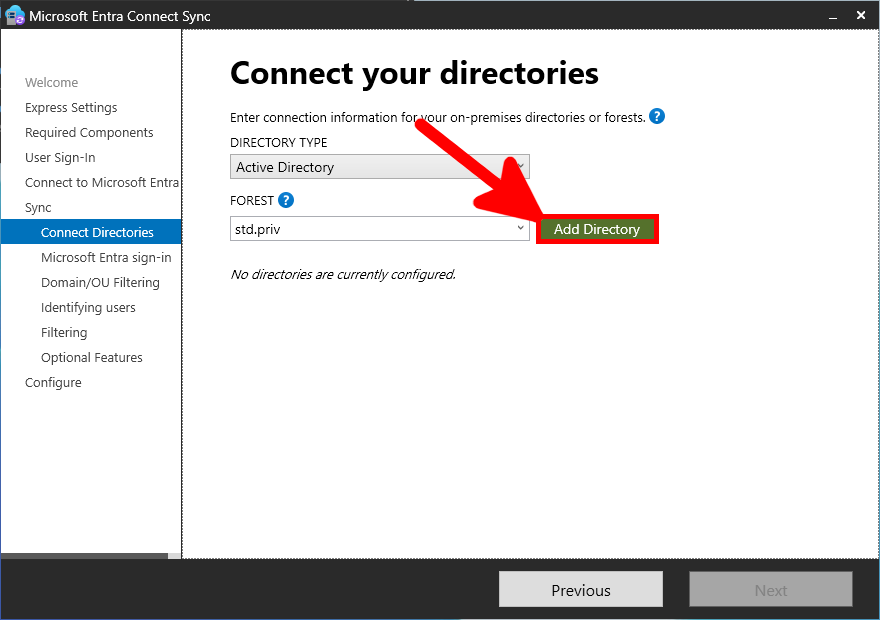
- On the Connect your directories page, select your on-premise forest, then click on Add Directory:
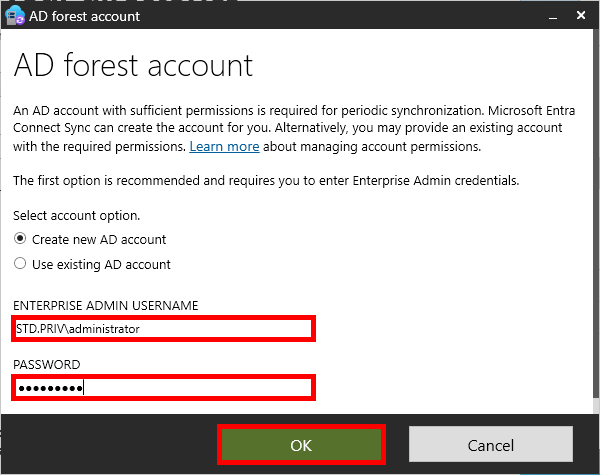
- In the AD forest account window, select the Create New AD Account option, and enter your domain administrator username and password to automatically create an account that will be used to synchronize user accounts and passwords:
- The on-premise domain should appear:
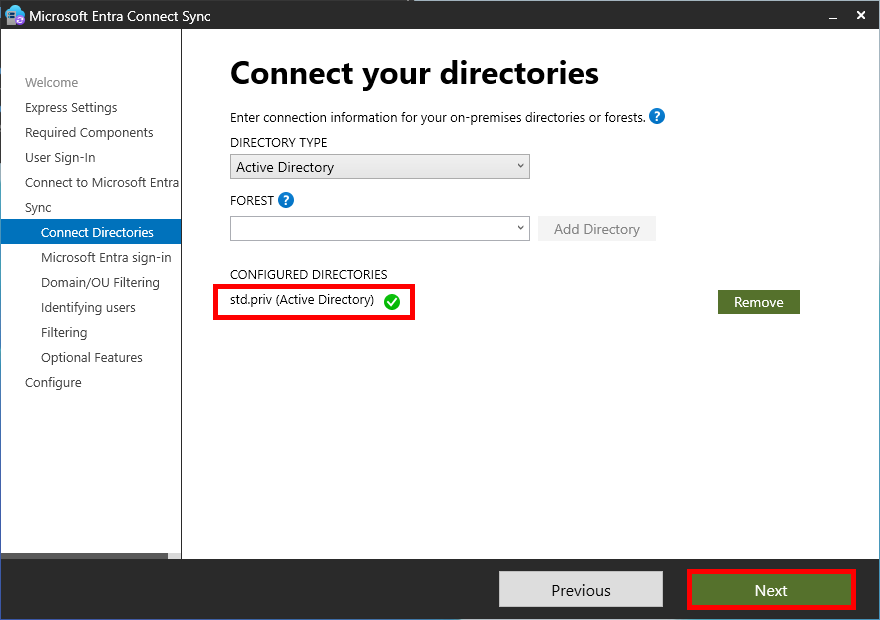
- As my on-premise domain is std.priv, we cannot use userPrincipalName as an attribute on the Entra ID sign-in configuration page, please ensure that the value mail is selected in the USER PRINCIPAL NAME drop-down list. Also check the Continue without matching all UPN suffixes to verified domains box and click Next:
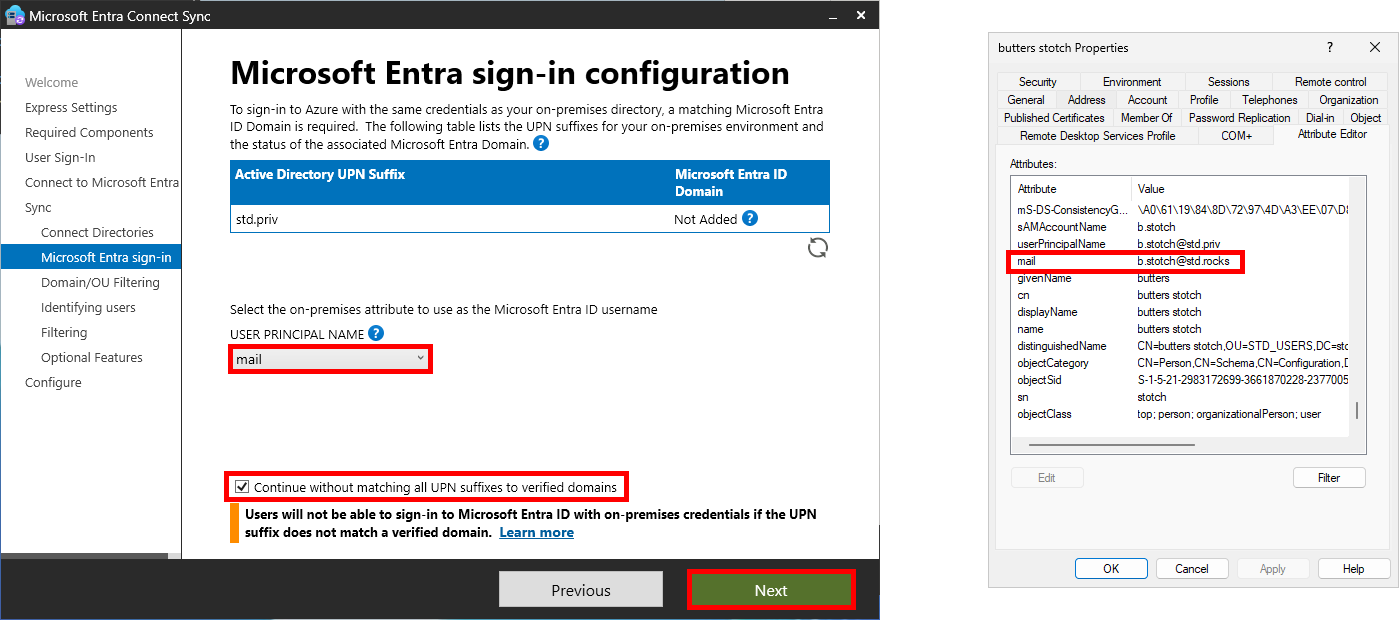
- On the Domain and OU filtering page, select Sync selected domains and OUs and expend your domain. Then check the Active Directory OU containing the user accounts you wish to synchronize:
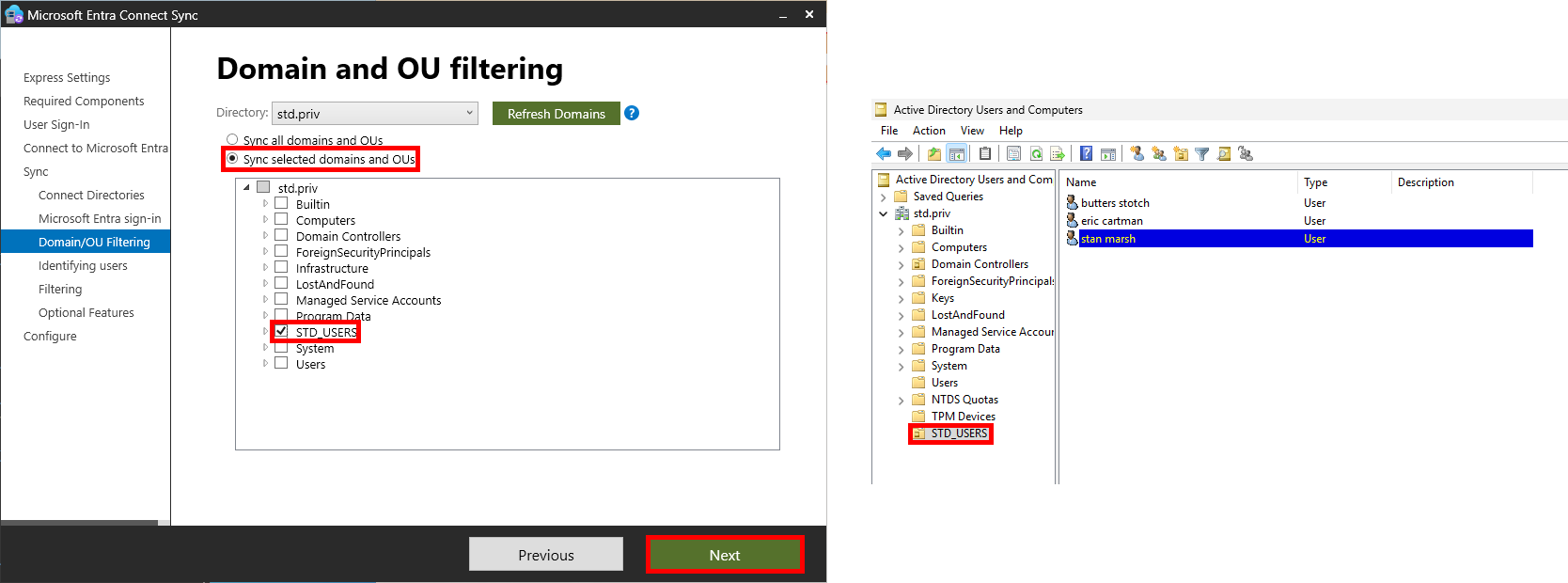
- On the Uniquely identifying your users page, click on Next:
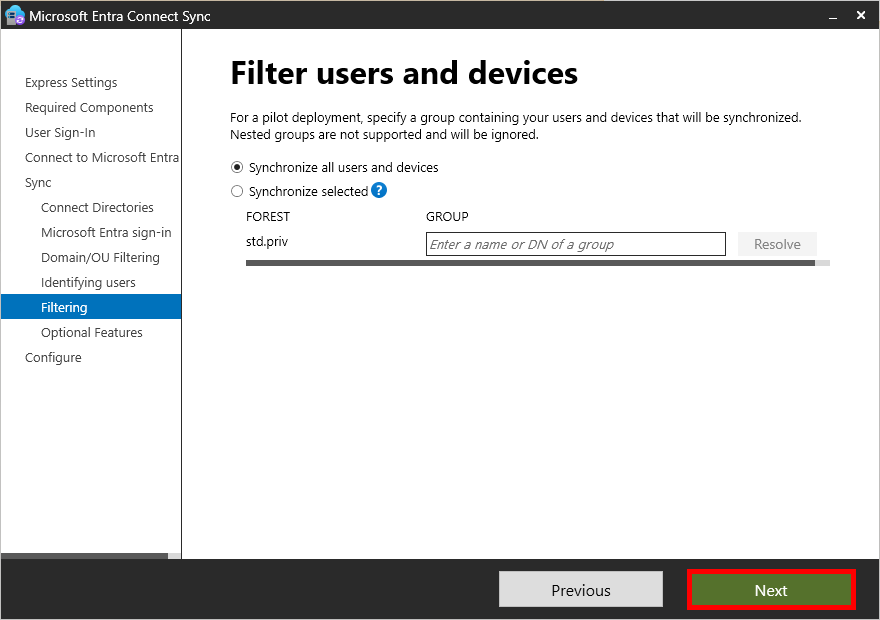
- On the Filter users and devices page, click on Next:
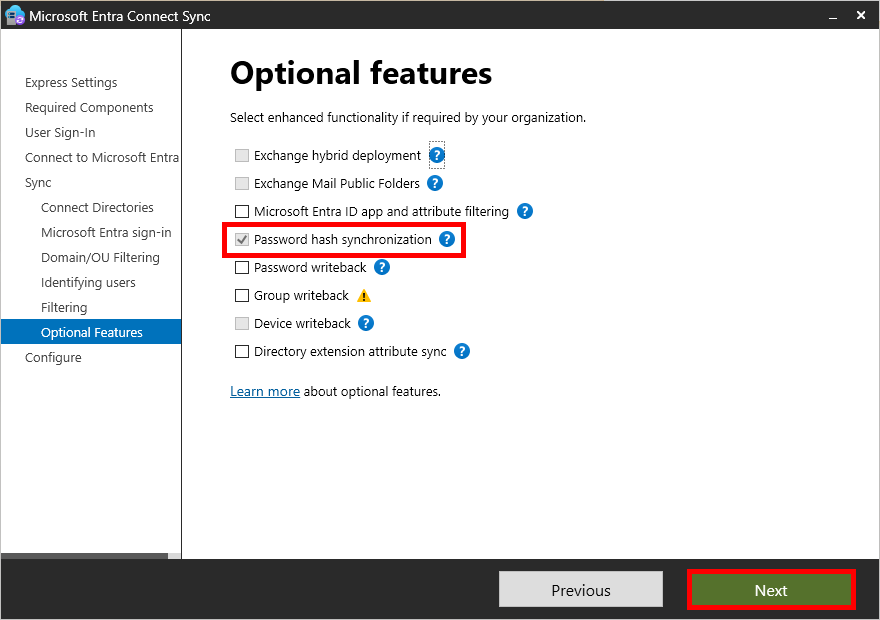
- On the Optional features page, Password hash synchronization should be selected. Click on Next:
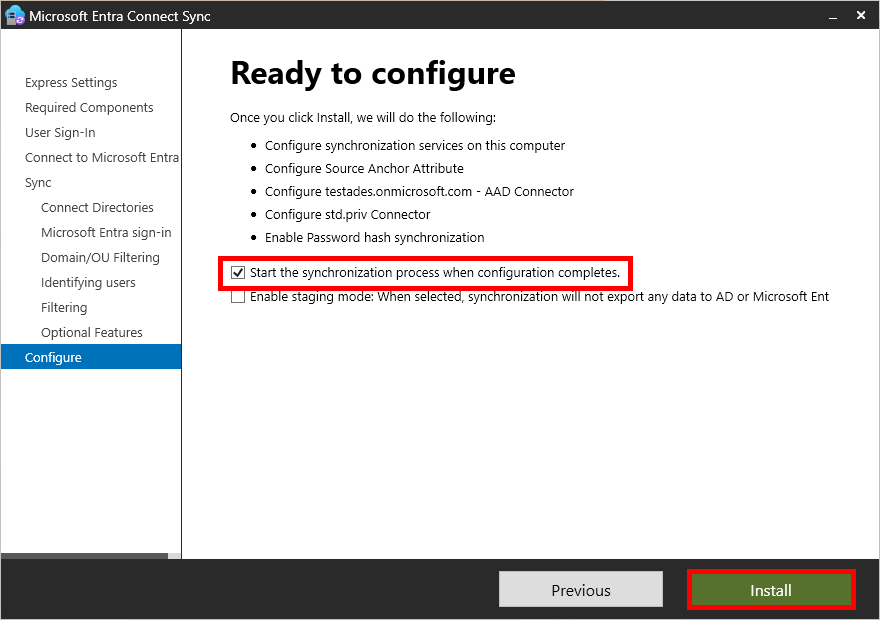
- On the Ready to configure page, check Start the synchronization process when configuration completes, then click on Install:
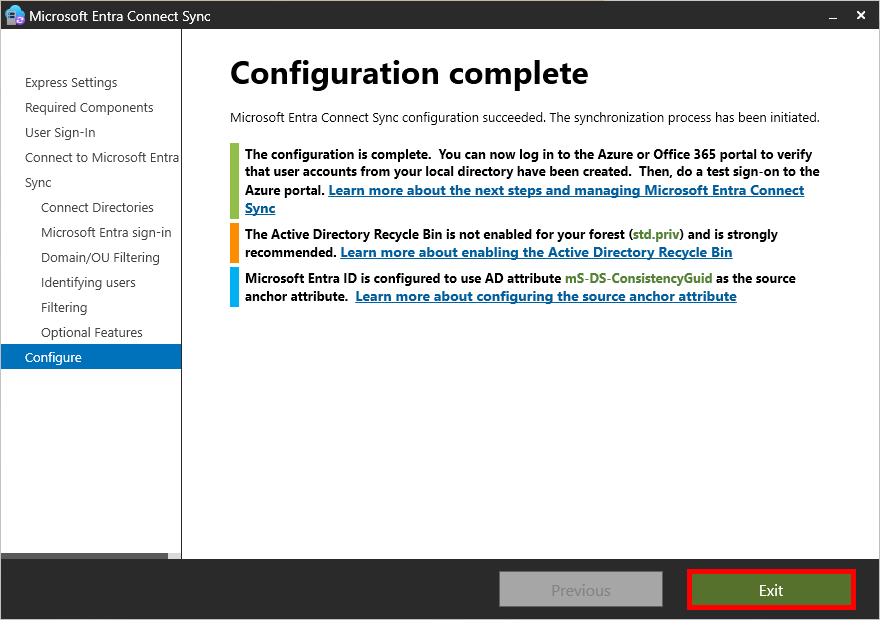
- Once installation is complete, click on Exit:
- Log in to Entra ID and check that your users accounts have been created:
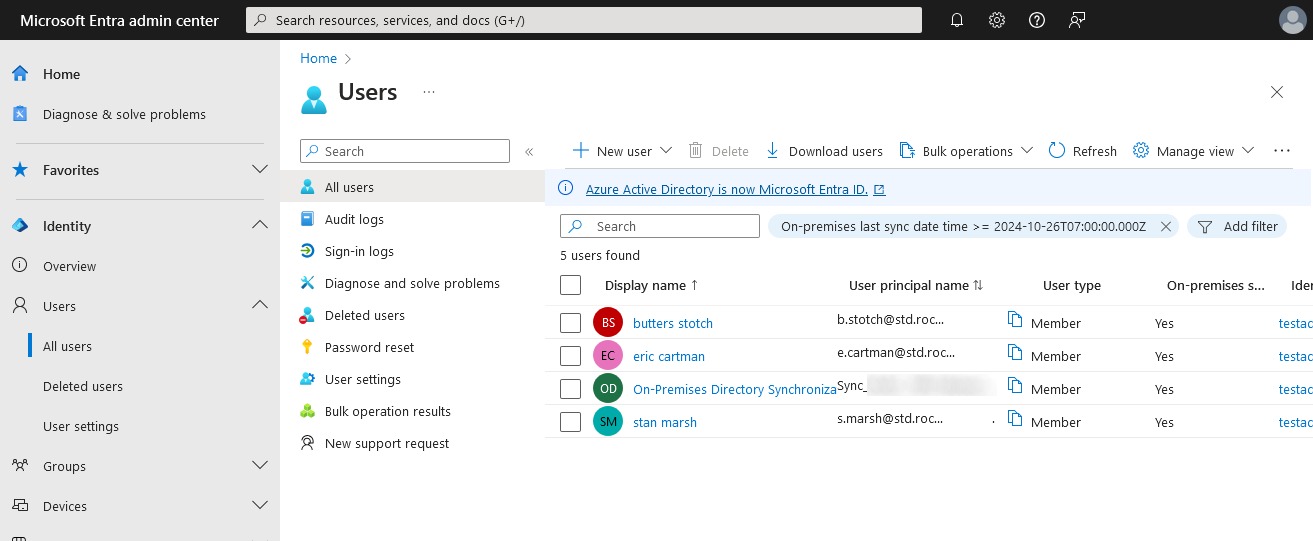
- Note that you can perform a manual synchronization with this PowerShell command (use the Policytype Initial parameter to perform a full synchronization):
PS C:\> Start-ADSyncSyncCycle -PolicyType Delta