
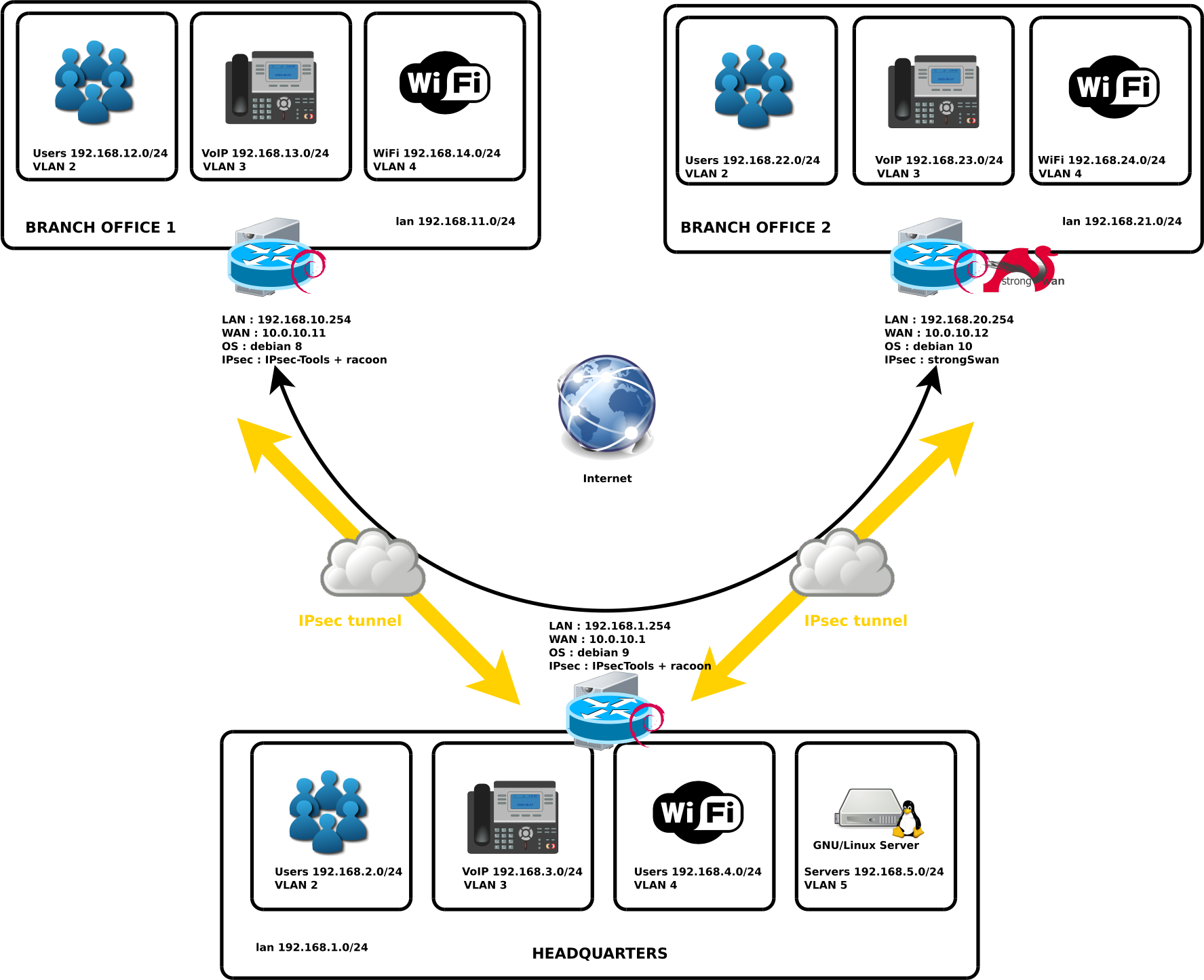
I will put here complete Multi-site IPsec VPN configuration that I had to set up.
root@host:~# apt install ipsec-tools racoon nftables
root@host:~# systemctl enable nftables.service
#!/usr/sbin/nft -f
flush ruleset
table inet filter {
chain input {
type filter hook input priority 0; policy accept;
}
chain forward {
type filter hook forward priority 0; policy accept ;
}
chain output {
type filter hook output priority 0; policy accept;
}
}
table ip my_nat {
chain my_masquerade {
type nat hook postrouting priority 100;
ip daddr != { 10.0.10.11, 192.168.0.0/16 } oifname wan masquerade comment "output nat"
}
}
# This file describes the network interfaces available on your system # and how to activate them. For more information, see interfaces(5). source /etc/network/interfaces.d/* # The loopback network interface auto lo iface lo inet loopback # The primary network interface # This is an autoconfigured IPv6 interface allow-hotplug wan iface wan inet static address 10.0.10.1 netmask 255.255.255.0 gateway 10.0.10.254 allow-hotplug lan iface lan inet static address 192.168.1.254 netmask 255.255.255.0 up /usr/local/sbin/ipconf.sh
#!/bin/sh ##NETWORK INTERFACES ip link add link lan name users type vlan id 2 ip link add link lan name voip type vlan id 3 ip link add link lan name wifi type vlan id 4 ip link add link lan name servers type vlan id 5 ip link set users up ip link set voip up ip link set wifi up ip link set servers up ip addr add 192.168.2.254/24 dev users ip addr add 192.168.3.254/24 dev voip ip addr add 192.168.4.254/22 dev wifi ip addr add 192.168.5.254/24 dev servers ##ROUTES #BRANCH OFFICE 1 ip route add 192.168.12.0/24 via 192.168.1.254 src 192.168.1.254 ip route add 192.168.13.0/24 via 192.168.1.254 src 192.168.1.254 #BRANCH OFFICE 2 ip route add 192.168.22.0/24 via 192.168.1.254 src 192.168.1.254 ip route add 192.168.23.0/24 via 192.168.1.254 src 192.168.1.254 #ENABLE ROUTING sysctl net.ipv4.ip_forward=1 echo "1" > /proc/sys/net/netfilter/nf_conntrack_acct #RESTART SERVICES systemctl restart racoon setkey -f /etc/ipsec-tools.conf systemctl restart nftables
root@host:~# chmod +x /usr/local/sbin/ipconf.sh
log debug; path pre_shared_key "/etc/racoon/psk.txt"; # phase 1 / BRANCH OFFICE 1 remote 10.0.10.11 { exchange_mode main,aggressive; my_identifier address 10.0.10.1; proposal_check obey; proposal { authentication_method pre_shared_key; encryption_algorithm aes128; hash_algorithm sha1; dh_group 1; } generate_policy off; } # phase 1 / BRANCH OFFICE 2 remote 10.0.10.12 { exchange_mode main; my_identifier address 10.0.10.1; proposal_check obey; proposal { authentication_method pre_shared_key; encryption_algorithm aes128; hash_algorithm sha1; dh_group 1; } generate_policy off; } # phase 2 sainfo anonymous { pfs_group 1; lifetime time 12 hour ; encryption_algorithm aes128; authentication_algorithm hmac_sha1; compression_algorithm deflate ; }
10.0.10.11 password_PSK4231 10.0.10.12 password_PSK4231
#!/usr/sbin/setkey -f
flush;
spdflush;
##HEADQUARTERS <-> BRANCH OFFICE 1
#lan to lan
spdadd 192.168.1.0/24 192.168.11.0/24 any -P out ipsec
esp/tunnel/10.0.10.1-10.0.10.11/unique;
spdadd 192.168.11.0/24 192.168.1.0/24 any -P in ipsec
esp/tunnel/10.0.10.11-10.0.10.1/unique;
#VoIP
spdadd 192.168.3.0/24 192.168.13.0/24 any -P out ipsec
esp/tunnel/10.0.10.1-10.0.10.11/unique;
spdadd 192.168.13.0/24 192.168.3.0/24 any -P in ipsec
esp/tunnel/10.0.10.11-10.0.10.1/unique;
#Users and Servers
spdadd 192.168.5.0/24 192.168.12.0/24 any -P out ipsec
esp/tunnel/10.0.10.1-10.0.10.11/unique;
spdadd 192.168.12.0/24 192.168.5.0/24 any -P in ipsec
esp/tunnel/10.0.10.11-10.0.10.1/unique;
##BRANCH OFFICE 2 <-> BRANCH OFFICE 1
#BRANCH OFFICE 1 (10.0.10.11) <-> HEADQUARTERS (10.0.10.1)
spdadd 192.168.23.0/24 192.168.13.0/24 any -P out ipsec
esp/tunnel/10.0.10.1-10.0.10.11/unique;
spdadd 192.168.13.0/24 192.168.23.0/24 any -P in ipsec
esp/tunnel/10.0.10.11-10.0.10.1/unique;
#BRANCH OFFICE 2 (10.0.10.12) <-> HEADQUARTERS (10.0.10.1)
spdadd 192.168.13.0/24 192.168.23.0/24 any -P out ipsec
esp/tunnel/10.0.10.1-10.0.10.12/unique;
spdadd 192.168.23.0/24 192.168.13.0/24 any -P in ipsec
esp/tunnel/10.0.10.12-10.0.10.1/unique;
##HEADQUARTERS <-> BRANCH OFFICE 2
#lan to lan
spdadd 192.168.1.0/24 192.168.21.0/24 any -P out ipsec
esp/tunnel/10.0.10.1-10.0.10.12/unique;
spdadd 192.168.21.0/24 192.168.1.0/24 any -P in ipsec
esp/tunnel/10.0.10.12-10.0.10.1/unique;
#VoIP
spdadd 192.168.3.0/24 192.168.23.0/24 any -P out ipsec
esp/tunnel/10.0.10.1-10.0.10.12/unique;
spdadd 192.168.23.0/24 192.168.3.0/24 any -P in ipsec
esp/tunnel/10.0.10.12-10.0.10.1/unique;
root@host:~# systemctl restart racoon
root@host:~# apt install ipsec-tools racoon
# This file describes the network interfaces available on your system # and how to activate them. For more information, see interfaces(5). source /etc/network/interfaces.d/* # The loopback network interface auto lo iface lo inet loopback # The primary network interface # This is an autoconfigured IPv6 interface auto wan iface wan inet static address 10.0.10.11 netmask 255.255.255.0 up /usr/local/sbin/ipconf.sh allow-hotplug lan iface lan inet static address 192.168.11.254 netmask 255.255.255.0
#!/bin/sh ##REINIT IPTABLES RULES iptables -F iptables -X iptables -t nat -F iptables -t nat -X iptables -t mangle -F iptables -t mangle -X iptables -P INPUT ACCEPT iptables -P FORWARD ACCEPT iptables -P OUTPUT ACCEPT modprobe nf_conntrack_ftp modprobe nf_nat_ftp ##NETWORK INTERFACES modprobe 8021q ip link add link lan name users type vlan id 2 ip link add link lan name voip type vlan id 3 ip link add link lan name wifi type vlan id 4 ip link set users up ip link set voip up ip link set wifi up ip addr add 192.168.12.254/24 dev users ip addr add 192.168.13.254/24 dev voip ip addr add 192.168.14.254/24 dev wifi echo 1 >/proc/sys/net/ipv4/ip_forward ##ROUTES #HEADQUARTERS ip route add 192.168.1.0/24 via 192.168.11.254 src 192.168.11.254 ip route add 192.168.3.0/24 via 192.168.13.254 src 192.168.13.254 ip route add 192.168.5.0/24 via 192.168.12.254 src 192.168.12.254 #BRANCH OFFICE 2 ip route add 192.168.23.0/24 via 192.168.13.254 src 192.168.13.254 ##IPTABLES #NOT NEEDED AS WE ACCEPT ANY BUT GOOD TO KNOW iptables -A INPUT -s 10.0.10.1 -j ACCEPT iptables -A INPUT -p esp -j ACCEPT iptables -A INPUT -p udp --dport 500 -j ACCEPT iptables -A OUTPUT -p esp -j ACCEPT iptables -A OUTPUT -p udp --sport 500 -j ACCEPT #AVOID IPsec trafic to be translated inside nat iptables -t nat -A POSTROUTING -d 192.168.1.0/24 -m policy --dir out --pol ipsec -j ACCEPT iptables -t nat -A POSTROUTING -d 192.168.3.0/24 -m policy --dir out --pol ipsec -j ACCEPT iptables -t nat -A POSTROUTING -d 192.168.5.0/24 -m policy --dir out --pol ipsec -j ACCEPT iptables -t nat -A POSTROUTING -d 192.168.23.0/24 -m policy --dir out --pol ipsec -j ACCEPT
log debug; path pre_shared_key "/etc/racoon/psk.txt"; # phase 1 / HEADQUARTERS remote 10.0.10.1 { exchange_mode main,aggressive; my_identifier address 10.0.10.11; proposal_check obey; proposal { authentication_method pre_shared_key; encryption_algorithm aes128; hash_algorithm sha1; dh_group 1; } generate_policy off; } # phase 2 sainfo anonymous { pfs_group 1; lifetime time 12 hour ; encryption_algorithm aes128; authentication_algorithm hmac_sha1; compression_algorithm deflate ; }
10.0.10.1 password_PSK4231
#!/usr/sbin/setkey -f
flush;
spdflush;
##BRANCH OFFICE 1 <-> HEADQUARTERS
#VoIP
spdadd 192.168.13.0/24 192.168.3.0/24 any -P out ipsec
esp/tunnel/10.0.10.11-10.0.10.1/unique;
spdadd 192.168.3.0/24 192.168.13.0/24 any -P in ipsec
esp/tunnel/10.0.10.1-10.0.10.11/unique;
#Users and Servers
spdadd 192.168.12.0/24 192.168.5.0/24 any -P out ipsec
esp/tunnel/10.0.10.11-10.0.10.1/unique;
spdadd 192.168.5.0/24 192.168.12.0/24 any -P in ipsec
esp/tunnel/10.0.10.1-10.0.10.11/unique;
##BRANCH OFFICE 1 <-> BRANCH OFFICE 2
#VoIP
spdadd 192.168.13.0/24 192.168.23.0/24 any -P out ipsec
esp/tunnel/10.0.10.11-10.0.10.1/unique;
spdadd 192.168.23.0/24 192.168.13.0/24 any -P in ipsec
esp/tunnel/10.0.10.1-10.0.10.11/unique;
root@host:~# /etc/init.d/racoon restart
root@host:~# apt install strongswan nftables
root@host:~# systemctl enable nftables.service
#!/usr/sbin/nft -f
flush ruleset
table inet filter {
chain input {
type filter hook input priority 0; policy accept;
}
chain forward {
type filter hook forward priority 0; policy accept ;
}
chain output {
type filter hook output priority 0; policy accept;
}
}
table ip my_nat {
chain my_masquerade {
type nat hook postrouting priority 100;
ip daddr != { 10.0.10.11, 192.168.0.0/16 } oifname wan masquerade comment "output nat"
}
}
# This file describes the network interfaces available on your system # and how to activate them. For more information, see interfaces(5). source /etc/network/interfaces.d/* # The loopback network interface auto lo iface lo inet loopback # The primary network interface allow-hotplug wan iface wan inet static address 10.0.10.12 netmask 255.255.255.0 allow-hotplug lan iface lan inet static address 192.168.21.254 netmask 255.255.255.0 up /usr/local/sbin/ipconf.sh
#!/bin/sh ip link add link lan name users type vlan id 2 ip link add link lan name voip type vlan id 3 ip link add link lan name wifi type vlan id 4 ip link set users up ip link set voip up ip link set wifi up ip addr add 192.168.22.254/24 dev users ip addr add 192.168.23.254/22 dev voip ip addr add 192.168.24.254/24 dev wifi sysctl net.ipv4.ip_forward=1 systemctl restart ipsec systemctl restart nftables
root@host:~# chmod +x /usr/local/sbin/ipconf.sh
# ipsec.conf - strongSwan IPsec configuration file
# basic configuration
conn office2
#charondebug = 2
authby = secret
auto = route
#auto=start #https://www.questioncomputer.com/ipsec-on-linux-strongswan-configuration-ikev2-policy-based-psk/
type = tunnel
keyexchange = ikev1
ike = aes128-sha1-modp768
esp = aes128-sha1-modp768
#BRANCH OFFICE 2
leftfirewall = yes
left = 10.0.10.12
leftid = 10.0.10.12
leftsubnet = 192.168.21.0/24
#HEADQUARTERS
rightfirewall = yes
rightid = 10.0.10.1
right = 10.0.10.1
rightsubnet = 192.168.1.0/24
conn net-users
also=office2
leftsubnet = 192.168.22.0/24
conn net-voip
also=office2
leftsubnet = 192.168.23.0/24
rightsubnet = 192.168.3.0/24
conn net-voip2
also=office2
leftsubnet = 192.168.23.0/24
rightsubnet = 192.168.13.0/24
: PSK password_PSK4231
root@host:~# systemctl restart ipsec.service
root@host:~# ping 192.168.21.254 -I 192.168.1.254
root@host:~# ping 192.168.5.254 -I 192.168.12.254
root@host:~# ping 192.168.13.254 -I 192.168.23.254
root@host:~# tail -f /var/log/syslog | grep "racoon\|charon"
Contact :