My Personal Notes on Microsoft Active Directory: Commands, Configuration, and Best Practices
- Last updated: Jan 25, 2025
Intro
I'll put here any notes I have on Active Directory. This will be a reminder for me, but I hope it will also be useful for others. Happy reading!
DNS Configuration
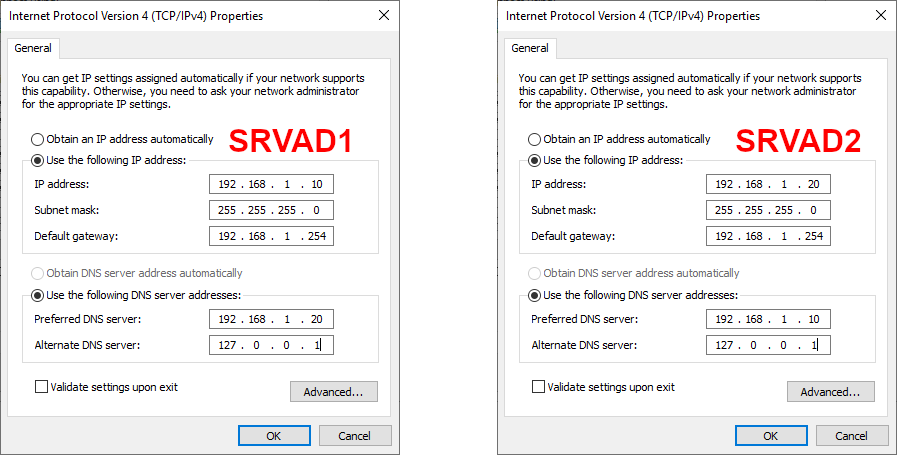
I can never remember the DNS definition order.
Suppose we have two AD servers:
- SRVAD1: 192.168.1.10
- SRVAD2: 192.168.1.20
What should be the correct DNS configuration? The answer is:
Commands
Tests
- Analyzes the status of domain controllers and reports any problems to facilitate troubleshooting:
PS C:\ > dcdiag
- Run dns, replications or netlogons tests only:
PS C:\ > dcdiag /test:dns
PS C:\ > dcdiag /test:replications
PS C:\ > dcdiag /test:netlogons
- Display replication status:
PS C:\ > repadmin /showrepl
- Identifies Domain Controllers whose inbound or outbound replication has failed and summarizes the results in a report:
PS C:\ > repadmin /replsum
Misc
- Synchronize a Domain Controller with all its replication partners:
PS C:\ > repadmin /syncall
Move fsmo roles
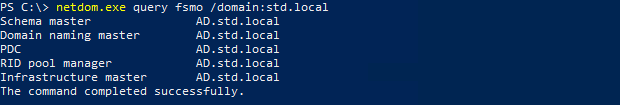
- Displays the current list of Operations Master Role holders and their associates servers:
PS C:\ > netdom query /domain:std.local fsmo
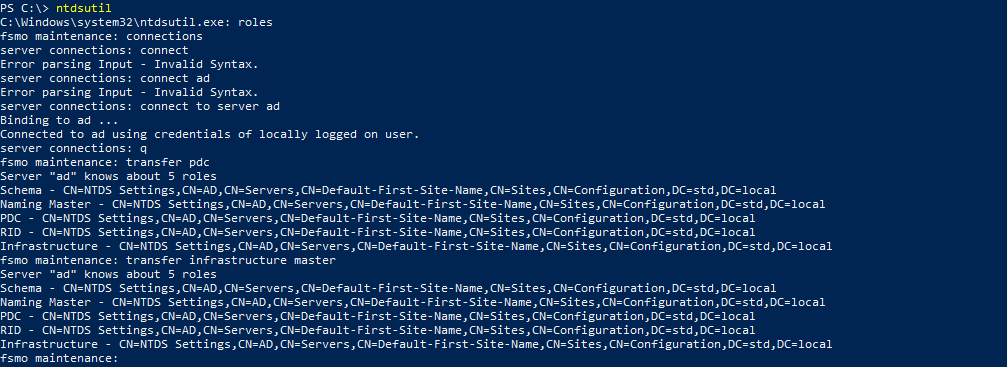
Dos method (old)
PS C:\ > ntdsutil
ntdsutil:
ntdsutil: roles
fsmo maintenance:
fsmo maintenance: connections
server connections:server connections: connect to server SRVAD
Binding to ad ...
Connected to ad using credentials of locally logged on user.
server connections:
server connections: q
fsmo maintenance:
Transfer naming master
Transfer infrastructure master
Transfer PDC
Transfer RID master
Transfer schema master
PowerShell method (New) :
- Check current configuration:
PS C:\ > Get-ADDomainController -Server SRVAD | Select-Object -ExpandProperty OperationMasterRoles
PS C:\ > Get-ADForest std.local -Server SRVAD | format-list schemamaster,domainnamingmaster
- Transfer FSMO roles in a single command:
PS C:\ > Move-ADDirectoryServerOperationMasterRole -Identity SRVAD -OperationMasterRole pdcemulator,ridmaster,infrastructuremaster,schemamaster,domainnamingmaster
Rename DC
⚠️ Renaming a DC is a sensitive operation, so make sure you have at least one backup and/or a second domain controller before making any changes. ⚠️
Check
- Lists the primary name or any alternate name:
PS C:\ > Netdom computername SRVAD /ENUMerate
- Checks wether a DNS record and a service principal name (SPN) exist for a computer name:
PS C:\ > Netdom computername SRVAD /verify
Fast but not very reliable
Here, we directly request the name change; if the process fails, we can brick our DC.
- Rename the DC:
PS C:\ > netdom renamecomputer SRVOLD /NewName:SRVAD
Slow but safer
Here, we add a secondary name first; if the process fails, we still have a valid name that should work.
- Add a secondary name:
PS C:\ > Netdom computername SRVAD /add:SRVAD2.std.local
- Make the secondary name the primary name:
PS C:\ > Netdom computername SRVAD /makeprimary:SRVAD2.std.local
- Remove old name:
PS C:\ > Netdom computername SRVAD2 /remove:SRVAD.std.local
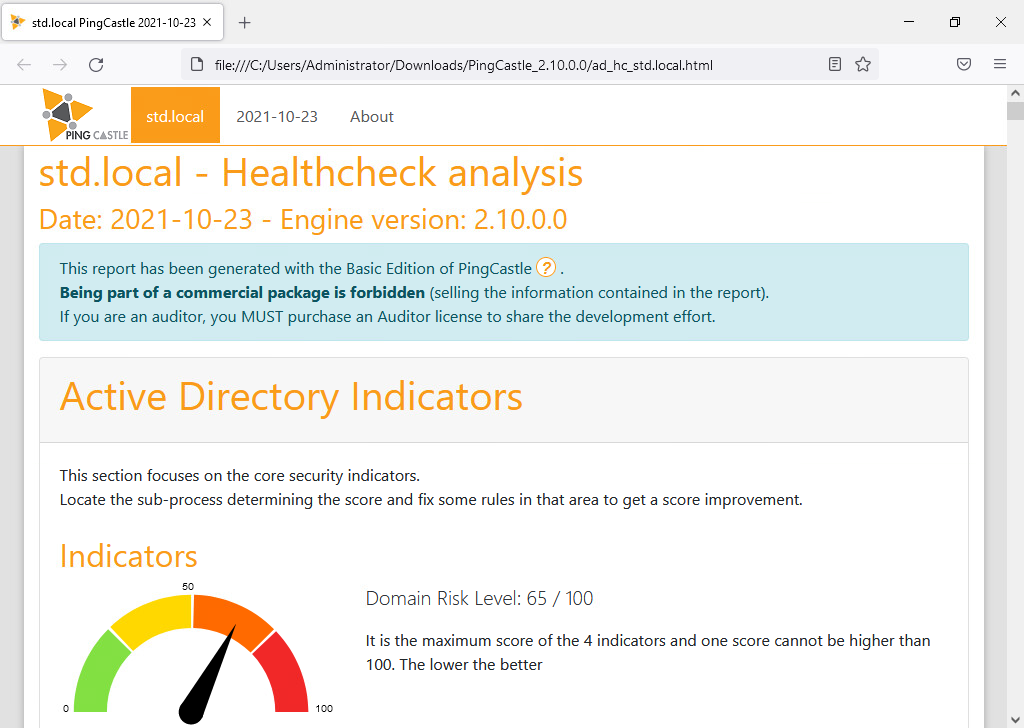
Hardening Active Directory
In its default configuration, Active Directory is not really secure. To strengthen its configuration, we can use the PingCastle tool.
- Go to the official page and download the tool:
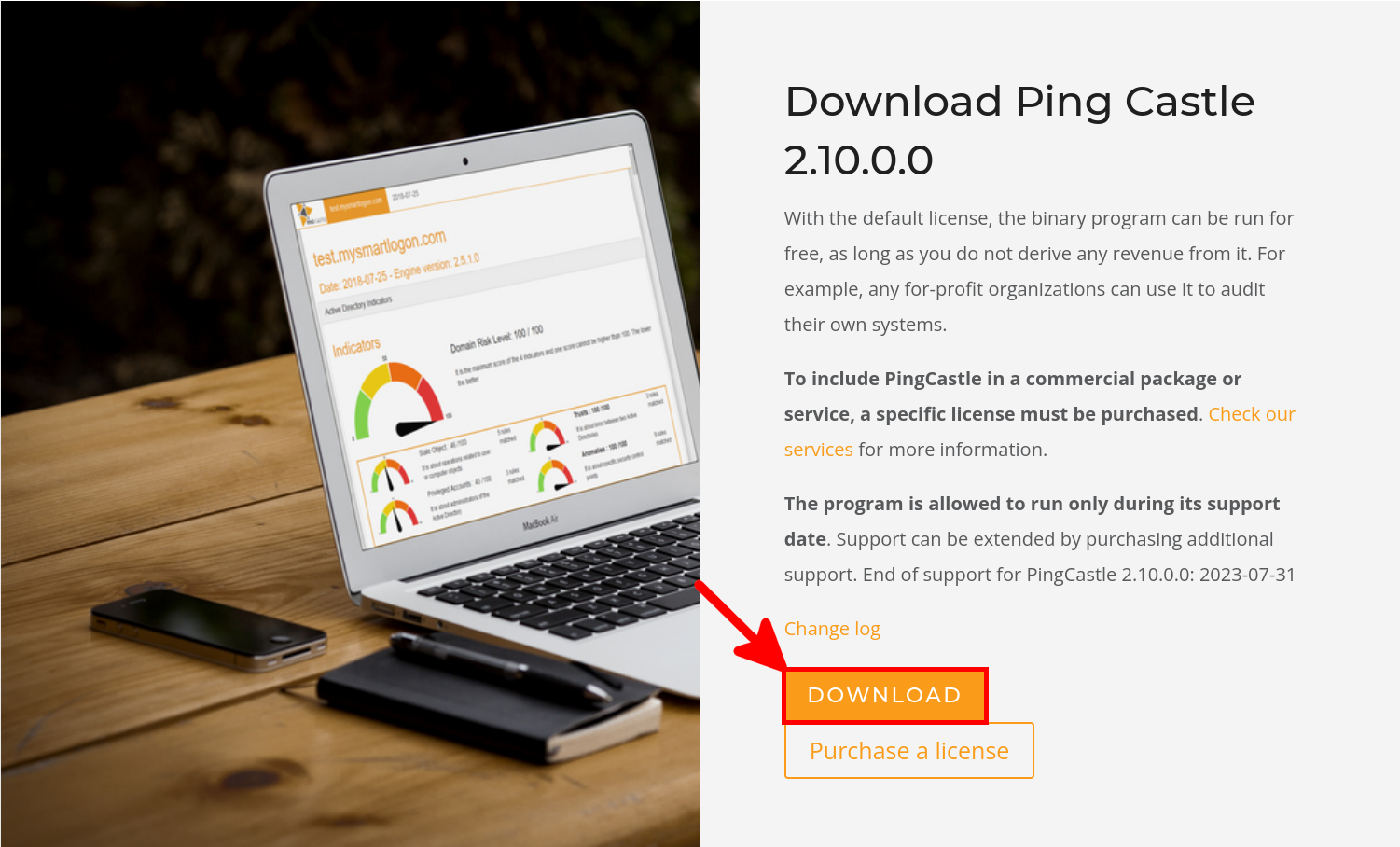
- Unzip and double-click PingCastle.exe to launch the tool:
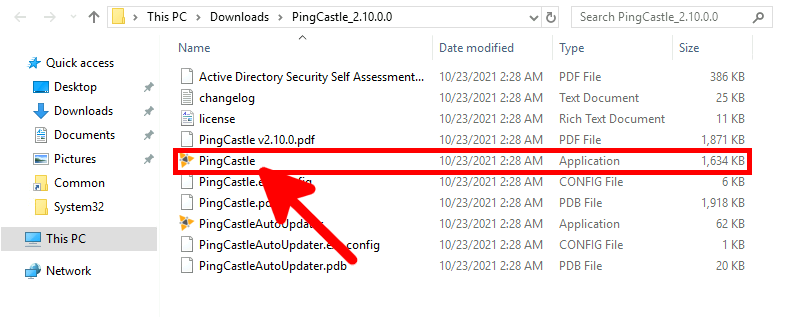
- Press Enter to check the score:
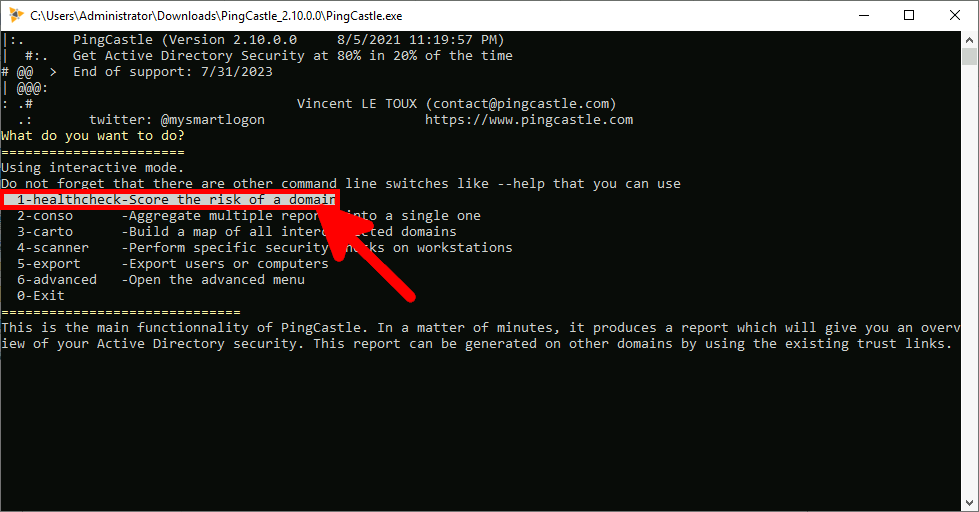
- Press Enter to investigate:
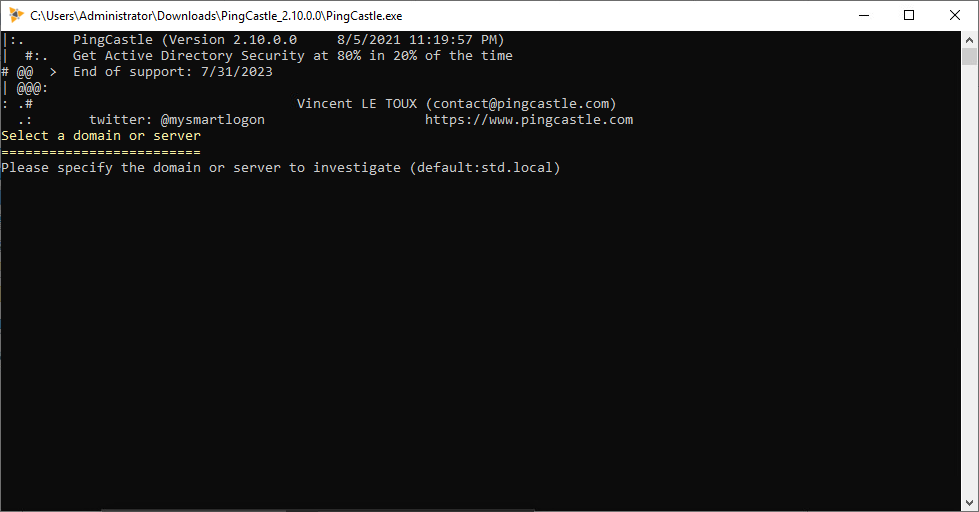
- When finished, press Enter to close the command prompt:
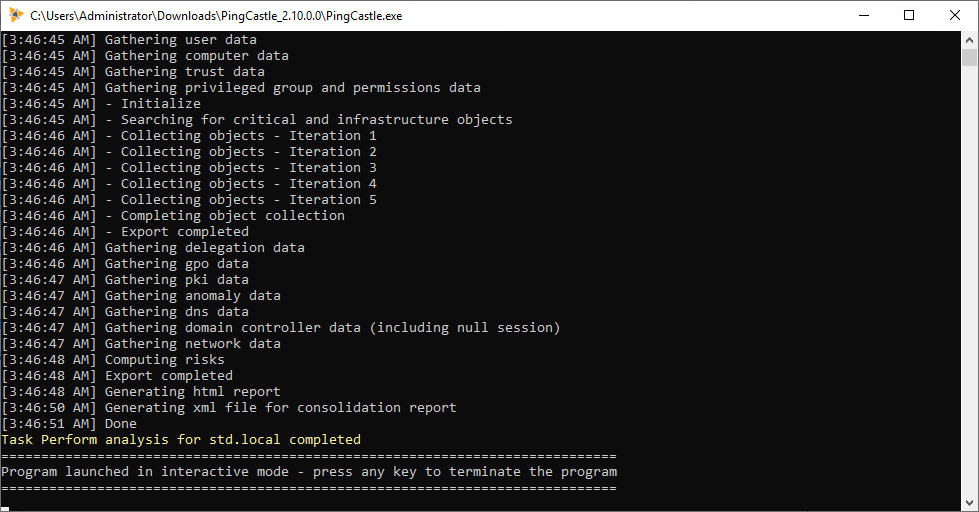
- Return to the unzipped folder and open the html report:
- Read the html report to correct any weaknesses: