Setting Up a Multi-Site IPsec VPN with strongSwan on Debian
- Last updated: Jan 19, 2025

I've already detailed in a previous article how to set up a multi-site IPsec VPN combining Racoon and strongSwan here: How to set up a Multi-site IPsec VPN with Racoon and strongSwan. As Racoon is now deprecated, I will describe here how to set up a multi-site IPsec VPN architecture, but only with strongSwan.
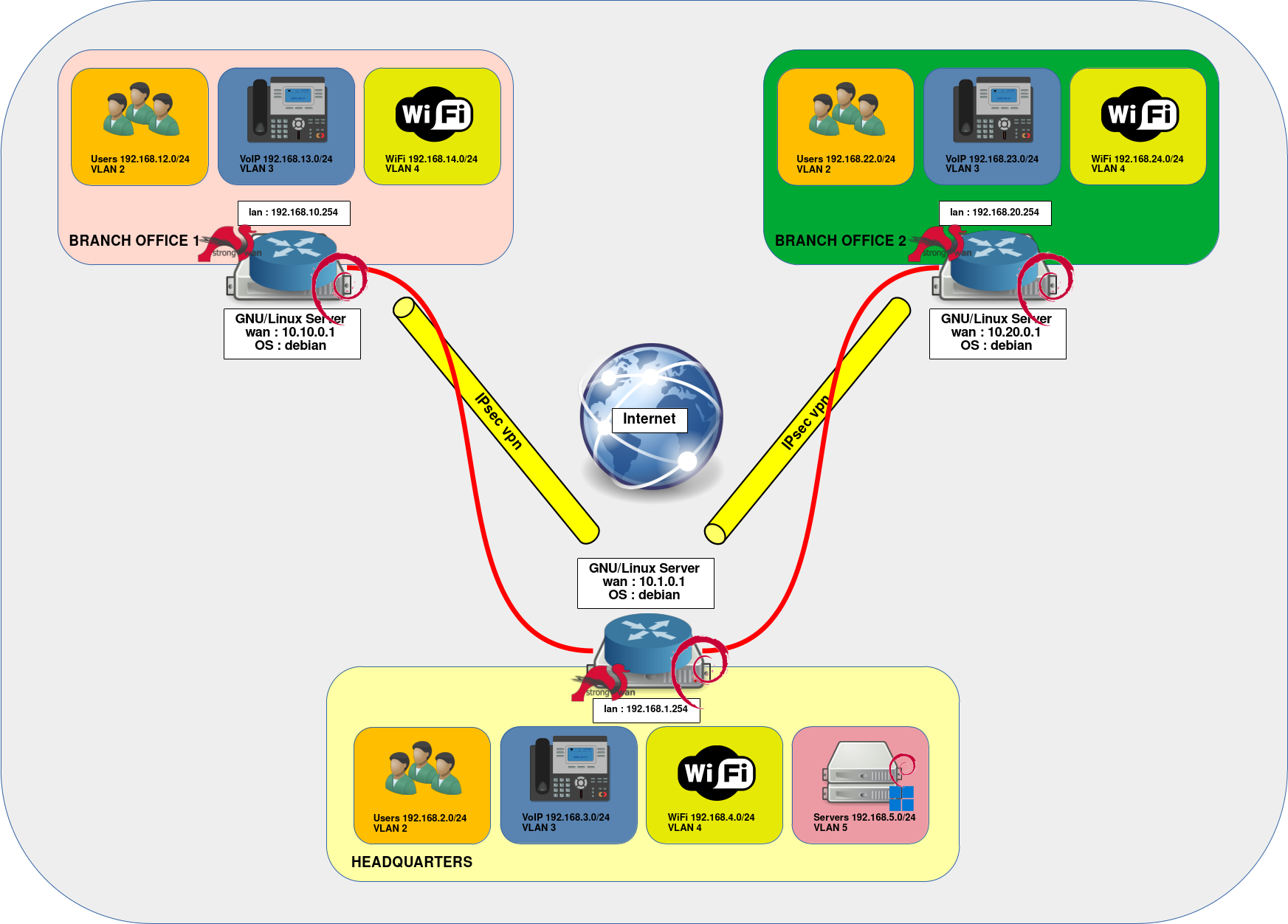
- The architecture presented in this guide consists of three routers on wich Debian and strongSwan are installed:
- The headquarters: the heart of the architecture, it comprises four networks, for users, IP phones, WiFi and application servers for internal users and those at other sites (branch office 1 and 2). It is also used as a VPN gateway for traffic between Branch Office 1 and Branch Office 2.
- Branch Office 1: consists of three networks: for users, IP phones and WiFi
- Branch Office 2: consists of three networks: for users, IP phones and WiFi
- Before you begin:
- We could have added an IPsec tunnel between Branch Office 1 and Branch Office 2 instead of using the Headquarters as a VPN gateway. However, as the traffic between the two branches is not significant (only IP phone communications), I didn't opt for this option.
Network Diagram
Site 1 - Headquarters
Let's start with the main site configuration. As a reminder, this is the site that centralizes vpn connections for all other sites, and it's also the site that “authorizes” connections (the VoIP network in this configuration) between Branch Office 1 and Branch Office 2.
Prerequisites
- Install the strongSwan package:
root@host:~# apt update && apt install strongswan- Enable
nftablesautostart:
root@host:~# systemctl enable nftables.servicenftables
The configuration of nftables is ultra-simplified here, allowing networks to access the Internet and communicate with each other. In a production environment, you may set up filtering between VLANs.
- Edit the
/etc/nftables.conffile:
#!/usr/sbin/nft -f
flush ruleset
table inet filter {
chain input {
type filter hook input priority 0; policy accept;
}
chain forward {
type filter hook forward priority 0; policy accept ;
}
chain output {
type filter hook output priority 0; policy accept;
}
}
#NAT for outgoing traffic.
table ip my_nat {
chain my_masquerade {
type nat hook postrouting priority 100;
ip daddr != { 10.1.0.1, 192.168.0.0/16 } oifname wan masquerade comment "output nat"
}
}- Reload the
nftablesconfiguration:
root@host:~# nft -f /etc/nftables.confNetwork configuration
Configure Network Interfaces
Here, we set up our two interfaces: lan and wan (Read this article to find out how to rename network interfaces under Debian: Renaming Network Interfaces on Debian).
- Edit the
/etc/network/interfacesfile:
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
source /etc/network/interfaces.d/*
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
# This is an autoconfigured IPv6 interface
allow-hotplug wan
iface wan inet static
address 10.1.0.1
netmask 255.255.255.0
gateway 10.1.0.254
allow-hotplug lan
iface lan inet static
address 192.168.1.254
netmask 255.255.255.0
up /usr/local/sbin/ipconf.sh- Reboot or restart the networking service:
root@host:~# systemctl restart networkingNetwork script
The /usr/local/sbin/ipconf.sh script will be executed at startup. It is used to configure the VLAN interfaces.
- Create a
/usr/local/sbin/ipconf.shfile:
#!/bin/sh
#SETTING UP VLANs ON THE lan INTERFACE
ip link add link lan name users type vlan id 2
ip link add link lan name voip type vlan id 3
ip link add link lan name wifi type vlan id 4
ip link add link lan name servers type vlan id 5
ip link set users up
ip link set voip up
ip link set wifi up
ip link set servers up
#VLAN INTERFACE IP ADDRESS SETTINGS
ip addr add 192.168.2.254/24 dev users
ip addr add 192.168.3.254/24 dev voip
ip addr add 192.168.4.254/22 dev wifi
ip addr add 192.168.5.254/24 dev servers
#ENABLE ROUTING
sysctl net.ipv4.ip_forward=1- Modify the rights so that the
/usr/local/sbin/ipconf.shscript is executable:
root@host:~# chmod +x /usr/local/sbin/ipconf.shstrongSwan
ipsec.conf
- Edit the
/etc/ipsec.conffile and configure the connections between the sites. The aim is to enable VoIP networks at all sites to communicate with each other. We're also enabling users at Branch Office 1 and Branch Office 2 to access the Headquarters server network:
#####################################
#Headquarters to Branch Office 1 setup#
#####################################
conn hq-b1
authby = secret
auto = route
type = tunnel
keyexchange = ikev2
ike = aes256-sha256-modp1024!
esp = aes256-sha256-modp1024!
#DPD
dpdaction=restart
dpddelay=300s
dpdtimeout=60s
#headquarters
leftfirewall = yes
leftid = 10.1.0.1
left = 10.1.0.1
leftsubnet = 192.168.1.0/24
#Branch Office 1
rightfirewall = yes
rightid = 10.10.0.1
right = 10.10.0.1
rightsubnet = 192.168.10.0/24
#VoIP - Headquarters and Branch Office 1
conn hq-b1-voip
also=hq-b1
leftsubnet = 192.168.3.0/24
rightsubnet = 192.168.13.0/24
#Servers/Headquarters and Users/Branch Office 1
conn hq-b1-servers
also=hq-b1
leftsubnet = 192.168.5.0/24
rightsubnet = 192.168.12.0/24
#VoIP/Branch Office 1 - Headquarters - VoIP/Branch Office 2
conn b1-hq-b2-voip
also=hq-b1
leftsubnet = 192.168.23.0/24
rightsubnet = 192.168.13.0/24
#####################################
#Headquarters to Branch Office 2 setup#
#####################################
conn hq-b2
authby = secret
auto = route
type = tunnel
keyexchange = ikev2
ike = aes256-sha256-modp1024!
esp = aes256-sha256-modp1024!
#DPD
dpdaction=restart
dpddelay=300s
dpdtimeout=60s
#Branch Office 2
rightfirewall = yes
rightid = 10.20.0.1
right = 10.20.0.1
rightsubnet = 192.168.20.0/24
#headquarters
leftfirewall = yes
leftid = 10.1.0.1
left = 10.1.0.1
leftsubnet = 192.168.1.0/24
#VoIP - Headquarters and Branch Office 2
conn hq-b2-voip
also=hq-b2
leftsubnet = 192.168.3.0/24
rightsubnet = 192.168.23.0/24
#Servers/Headquarters and Users/Branch Office 2
conn hq-b2-servers
also=hq-b2
leftsubnet = 192.168.5.0/24
rightsubnet = 192.168.22.0/24
#VoIP/Branch Office 2 - Headquarters - VoIP/Branch Office 1
conn b2-hq-b1-voip
also=hq-b2
rightsubnet = 192.168.23.0/24
leftsubnet = 192.168.13.0/24Configure the Preshared Key
We're going to set up our PSK (Pre-Shared Key), which will be used to authenticate the routers on the other sites.
- Edit the
/etc/ipsec.secretsfile:
: PSK password_PSK4231- Restart the
ipsecservice to take account of changes:
root@host:~# systemctl restart ipsec.serviceSite 2 - Branch Office 1
Let's move on to configuring the first of the branch office. The configuration is similar to that of the main site, since it also involves setting the network interfaces and the strongSwan service.
Prerequisites
- Install the strongSwan package:
root@host:~# apt update && apt install strongswan- Enable
nftablesautostart:
root@host:~# systemctl enable nftables.servicenftables
As with the main site, nftables configuration is simplified here. We won't be doing any filtering.
- Edit the
/etc/nftables.conffile:
#!/usr/sbin/nft -f
flush ruleset
table inet filter {
chain input {
type filter hook input priority 0; policy accept;
}
chain forward {
type filter hook forward priority 0; policy accept ;
}
chain output {
type filter hook output priority 0; policy accept;
}
}
#NAT for outgoing traffic.
table ip my_nat {
chain my_masquerade {
type nat hook postrouting priority 100;
ip daddr != { 10.10.0.1, 192.168.0.0/16 } oifname wan masquerade comment "output nat"
}
}- Reload the
nftablesconfiguration:
root@host:~# nft -f /etc/nftables.confNetwork Configuration
Configure Network Interfaces
We set up our two interfaces: lan and wan.
- Edit the
/etc/network/interfacesfile:
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
source /etc/network/interfaces.d/*
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
# This is an autoconfigured IPv6 interface
allow-hotplug wan
iface wan inet static
address 10.10.0.1
netmask 255.255.255.0
gateway 10.10.0.254
allow-hotplug lan
iface lan inet static
address 192.168.10.254
netmask 255.255.255.0
up /usr/local/sbin/ipconf.shNetwork script
The /usr/local/sbin/ipconf.sh script will be executed at startup. It is used to configure the VLAN interfaces.
- Create a
/usr/local/sbin/ipconf.shfile:
#!/bin/sh
#SETTING UP VLANs ON THE lan INTERFACE
modprobe 8021q
ip link add link lan name users type vlan id 2
ip link add link lan name voip type vlan id 3
ip link add link lan name wifi type vlan id 4
ip link set users up
ip link set voip up
ip link set wifi up
#VLAN INTERFACE IP ADDRESS SETTINGS
ip addr add 192.168.12.254/24 dev users
ip addr add 192.168.13.254/24 dev voip
ip addr add 192.168.14.254/22 dev wifi
#ENABLE ROUTING
sysctl net.ipv4.ip_forward=1- Modify the rights so that the
/usr/local/sbin/ipconf.shscript is executable:
root@host:~# chmod +x /usr/local/sbin/ipconf.shstrongSwan
ipsec.conf
- Edit the
/etc/ipsec.conffile:
#####################################
#Branch Office 1 to Headquarters setup#
#####################################
conn b1-hq
authby = secret
auto = route
type = tunnel
keyexchange = ikev2
ike = aes128-sha1-modp1024!
esp = aes128-sha1-modp1024!
#DPD
dpdaction=restart
dpddelay=300s
dpdtimeout=60s
#Branch Office 1
leftfirewall = yes
left = 10.10.0.1
leftid = 10.10.0.1
leftsubnet = 192.168.10.0/24
#headquarters
rightfirewall = yes
rightid = 10.1.0.1
right = 10.1.0.1
rightsubnet = 192.168.1.0/24
#VoIP - Branch Office 1 and Headquarters
conn b1-hq-voip
also=b1-hq
leftsubnet = 192.168.13.0/24
rightsubnet = 192.168.3.0/24
#Users/Branch Office 1 and Servers/Headquarters
conn b1-hq-servers
also=b1-hq
leftsubnet = 192.168.12.0/24
rightsubnet = 192.168.5.0/24
#VoIP/Branch Office 1 - Headquarters - VoIP/Branch Office 2
conn b1-hq-b2-voip
also=b1-hq
leftsubnet = 192.168.13.0/24
rightsubnet = 192.168.23.0/24Configure the Preshared Key
We'll use the same PSK (Pre-Shared Key) as for the main site.
- Edit the
/etc/ipsec.secretsfile:
: PSK password_PSK4231- Restart the
ipsecservice to take change into consideration:
root@host:~# systemctl restart ipsec.serviceSite 3 - Branch Office 2
Prerequisites
- Install the strongSwan package:
root@host:~# apt update && apt install strongswan- Enable
nftablesautostart:
root@host:~# systemctl enable nftables.servicenftables.conf
- Edit the
/etc/nftablesfile:
#!/usr/sbin/nft -f
flush ruleset
table inet filter {
chain input {
type filter hook input priority 0; policy accept;
}
chain forward {
type filter hook forward priority 0; policy accept ;
}
chain output {
type filter hook output priority 0; policy accept;
}
}
#NAT for outgoing traffic.
table ip my_nat {
chain my_masquerade {
type nat hook postrouting priority 100;
ip daddr != { 10.20.0.1, 192.168.0.0/16 } oifname wan masquerade comment "output nat"
}
}- Reload the
nftablesconfiguration:
root@host:~# nft -f /etc/nftables.confNetwork Configuration
Configure Network Interfaces
Here again, we set up our two interfaces (lan and wan).
- Edit the
/etc/network/interfacesfile:
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
source /etc/network/interfaces.d/*
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
allow-hotplug wan
iface wan inet static
address 10.20.0.1
netmask 255.255.255.0
allow-hotplug lan
iface lan inet static
address 192.168.21.254
netmask 255.255.255.0
up /usr/local/sbin/ipconf.shNetwork script
The /usr/local/sbin/ipconf.sh script will be executed at startup. It is used to configure the VLAN interfaces.
- Create a
/usr/local/sbin/ipconf.shfile:
#!/bin/sh
#SETTING UP VLANs ON THE lan INTERFACE
modprobe 8021q
ip link add link lan name users type vlan id 2
ip link add link lan name voip type vlan id 3
ip link add link lan name wifi type vlan id 4
ip link set users up
ip link set voip up
ip link set wifi up
#VLAN INTERFACE IP ADDRESS SETTINGS
ip addr add 192.168.22.254/24 dev users
ip addr add 192.168.23.254/24 dev voip
ip addr add 192.168.24.254/22 dev wifi
#ENABLE ROUTING
sysctl net.ipv4.ip_forward=1- Modify the rights so that the
/usr/local/sbin/ipconf.shscript is executable:
root@host:~# chmod +x /usr/local/sbin/ipconf.shstrongSwan
ipsec.conf
- Edit the
/etc/ipsec.conffile:
#####################################
#Branch Office 2 to Headquarters setup#
#####################################
conn b2-hq
authby = secret
auto = route
type = tunnel
keyexchange = ikev2
ike = aes128-sha1-modp1024!
esp = aes128-sha1-modp1024!
#DPD
dpdaction=restart
dpddelay=300s
dpdtimeout=60s
#Branch Office 2
leftfirewall = yes
left = 10.20.0.1
leftid = 10.20.0.1
leftsubnet = 192.168.20.0/24
#headquarters
rightfirewall = yes
rightid = 10.1.0.1
right = 10.1.0.1
rightsubnet = 192.168.1.0/24
#VoIP - Branch Office 2 and Headquarters
conn b2-hq-voip
also=b2-hq
leftsubnet = 192.168.23.0/24
rightsubnet = 192.168.3.0/24
#Users/Branch Office 2 and Servers/Headquarters
conn b2-hq-servers
also=b2-hq
leftsubnet = 192.168.22.0/24
rightsubnet = 192.168.5.0/24
#VoIP/Branch Office 2 - Headquarters - VoIP/Branch Office 1
conn b2-hq-b1-voip
also=b2-hq
leftsubnet = 192.168.23.0/24
rightsubnet = 192.168.13.0/24Configure the Preshared Key
We use the same PSK (Pre-Shared Key) as for other sites.
- Edit the
/etc/ipsec.secretsfile:
: PSK password_PSK4231- Restart the
ipsecservice to take change into consideration:
root@host:~# systemctl restart ipsec.serviceTroubleshooting
- Ping from Headquarters:
root@host:~# ping 192.168.21.254 -I 192.168.1.254- Ping from Branch Office 1:
root@host:~# ping 192.168.5.254 -I 192.168.12.254- Ping from Branch Office 2:
root@host:~# ping 192.168.13.254 -I 192.168.23.254- Check logs:
root@host:~# journalctl --grep "ipsec|charon"- Check IPsec connections and security associations (SA):
root@host:~# ipsec statusroot@host:~# ipsec statusall